In today's age, cyber threats are larger than ever, protecting sensitive data has become as crucial as locking your doors at night. Companies and individuals increasingly store their code on publicly accessible platforms like GitHub, where a single slip—like hardcoding sensitive information—can invite disaster. Rahasya steps in as a critical tool, designed to catch these common mistakes before they turn into major security breaches.
What is Rahasya?
Rahasya, derived from the Sanskrit word for "secret," is a cybersecurity tool designed to detect hard-coded secrets like API keys and passwords in your codebase before they can be exploited maliciously. It’s a Docker-driven tool that aims to simplify and enhance the security scanning process for developers and security engineers alike. It bundles some of the best open-source tools into one neat package, so you can run comprehensive scans with just a couple of clicks.
Why Rahasya?
We all know the drill—keeping sensitive info like API keys or passwords out of public view is cybersecurity 101. But let's be honest, scanning through code manually or setting up multiple tools can be a real drag. That’s where Rahasya comes in. Rahasya simplifies your life by wrapping several top-tier open-source tools into a single, user-friendly package.
For developers, Rahasya means less time configuring security tools and more time coding. It integrates seamlessly into the development process, offering a one-stop solution for security scans.
For security engineers, Rahasya provides a robust tool to perform thorough reviews and audits of codebases, ensuring compliance and security before and after deployment.
What’s Inside Rahasya?
Here’s the lowdown on what Rahasya brings to the party:
All-star lineup: Combining the strengths of GitLeaks, Gitty Leaks, TruffleHog, Detect Secrets, Git Guardian, and Talisman . Each specializing in detecting different types of exposed secrets
Custom scans: Not all projects are the same, right? Choose your arsenal with a simple flag, targeting exactly what you need, nothing more, nothing less.
Getting it Rolling
Git clone the repo that needs to be scanned.
Pull the tool from Docker Hub:
docker pull raikaustubh/rahasya
- Fire it up in your project's root directory:
docker run -it --rm -v "$(PWD):/repo" raikaustubh/rahasya
Want to scan using just GitLeaks, Gitty Leaks, TruffleHog, Detect Secrets, Git Guardian? Once the tool is run, just put the -scan flag and it will run all these tools. And if you want to run a scan exclusively with Talisman against the repo, then run the docker image and use the -include_talisman flag.
If you want to run a scan using a single tool or a combination from the features listed, that can be accomplished by using the -scan tool1 or -scan tool1 tool2 flag.
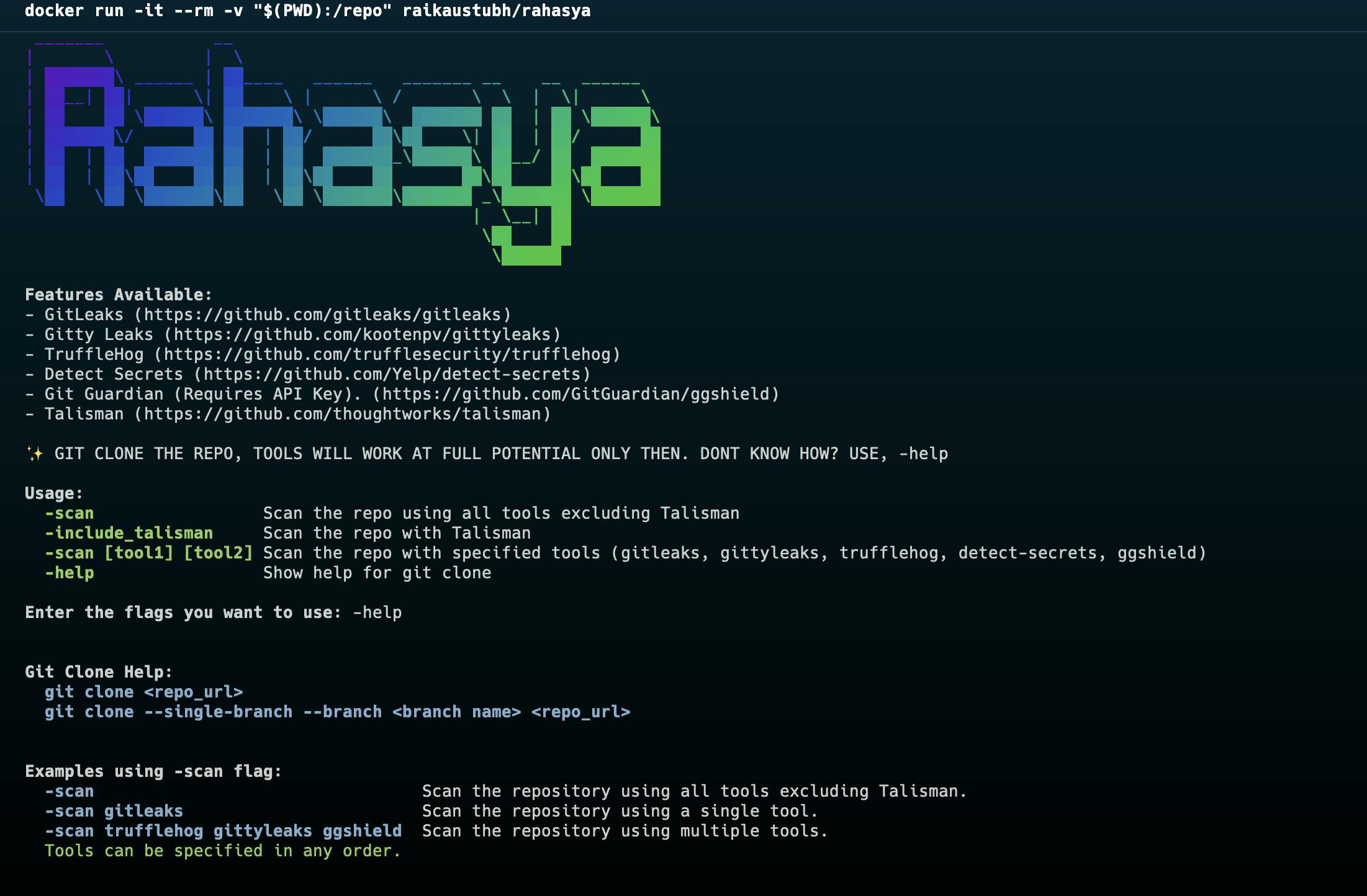
After the scan, you'll find each tool’s findings neatly organized in separate files within a local directory—clear, concise, and easy to review.
Customization
For the tinkerers and customisers, Rahasya’s Dockerfile is open for tweaking. Grab the code, splice in your API keys for GitGuardian, or switch up the tools to fit your exact needs.
Contribution
Got an idea? Throw in your two cents and help make Rahasya even better. Contribute to the repo.
Eager to level up your project’s security with minimal fuss? Give Rahasya a spin and tell those secrets to scram. Here’s to making our digital world a safer place, one scan at a time! ☮️
