Pentesting APIs: A Comprehensive Guide
Unraveling the Depths of API Technology, Penetration Testing, and Automation for Robust Security
Table of contents
- Introduction :
- What is API?
- Types of API :
- OWASP Top 10 API Security Risks :
- Client Pre-requisite :
- Setting Up Burp Suite for API Pentesting :
- 1. Download and Install Burp Suite.
- 2. Download and Install Postman.
- 3. In Postman, go to "Settings" and then "Proxy."
- 4. Set the proxy to 127.0.0.1 the port you noted in Burp Suite (usually 8080).
- 5. Sometimes by default SSL verification is enabled in Postman. Go to general and turn it off.
- 6. Verify IP and port in BurpSuite.
- 7. Now, when you send requests from Postman, Burp Suite will intercept them, allowing you to analyze and manipulate the requests and responses.
- Automating API Pentesting :
- Conclusion :
- References :
Introduction :
In the ever-evolving realm of technology, Application Programming Interfaces (APIs) have emerged as the backbone of seamless data exchange between applications. This blog aims to provide a comprehensive understanding of APIs, exploring their types, specifically SOAP and REST, unraveling the differences between them, delving into the API OWASP Top 10, and outlining the process of API penetration testing using Postman. We'll also explore common vulnerabilities, and tools for automating API penetration testing, and conclude with the importance of robust API security practices.
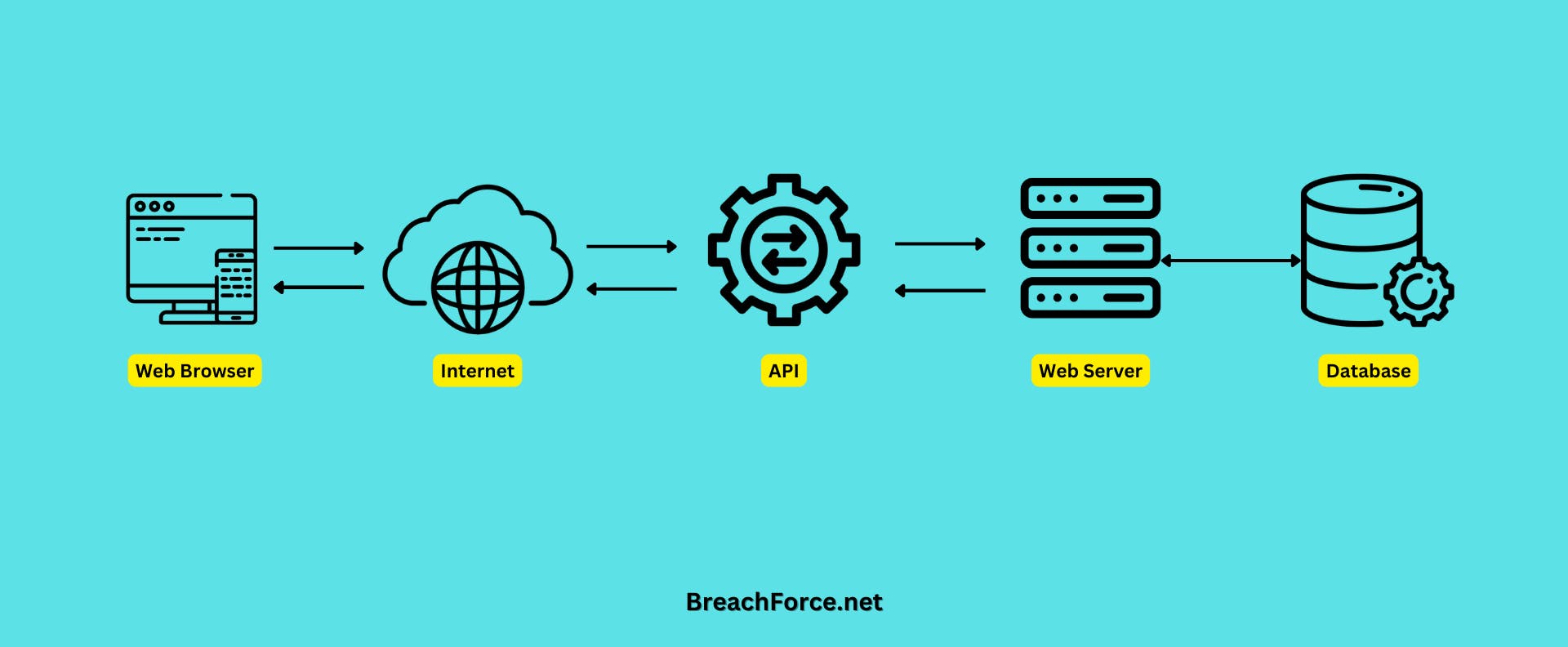
What is API?
An Application Programming Interface (API) acts as a bridge between different software systems, allowing them to communicate and share data. APIs define the methods and data formats applications can use to request and exchange information. They play a crucial role in modern software development, enabling seamless integration and interoperability.
Types of API :
In the complex landscape of application development, REST (Representational State Transfer) and SOAP (Simple Object Access Protocol) APIs stand out as two distinct architectural styles, each with its own set of characteristics. We will go through a detailed exploration of REST and SOAP APIs, offering clear definitions, highlighting key differences, and providing examples to illustrate their usage.
1. REST API: Representational State Transfer
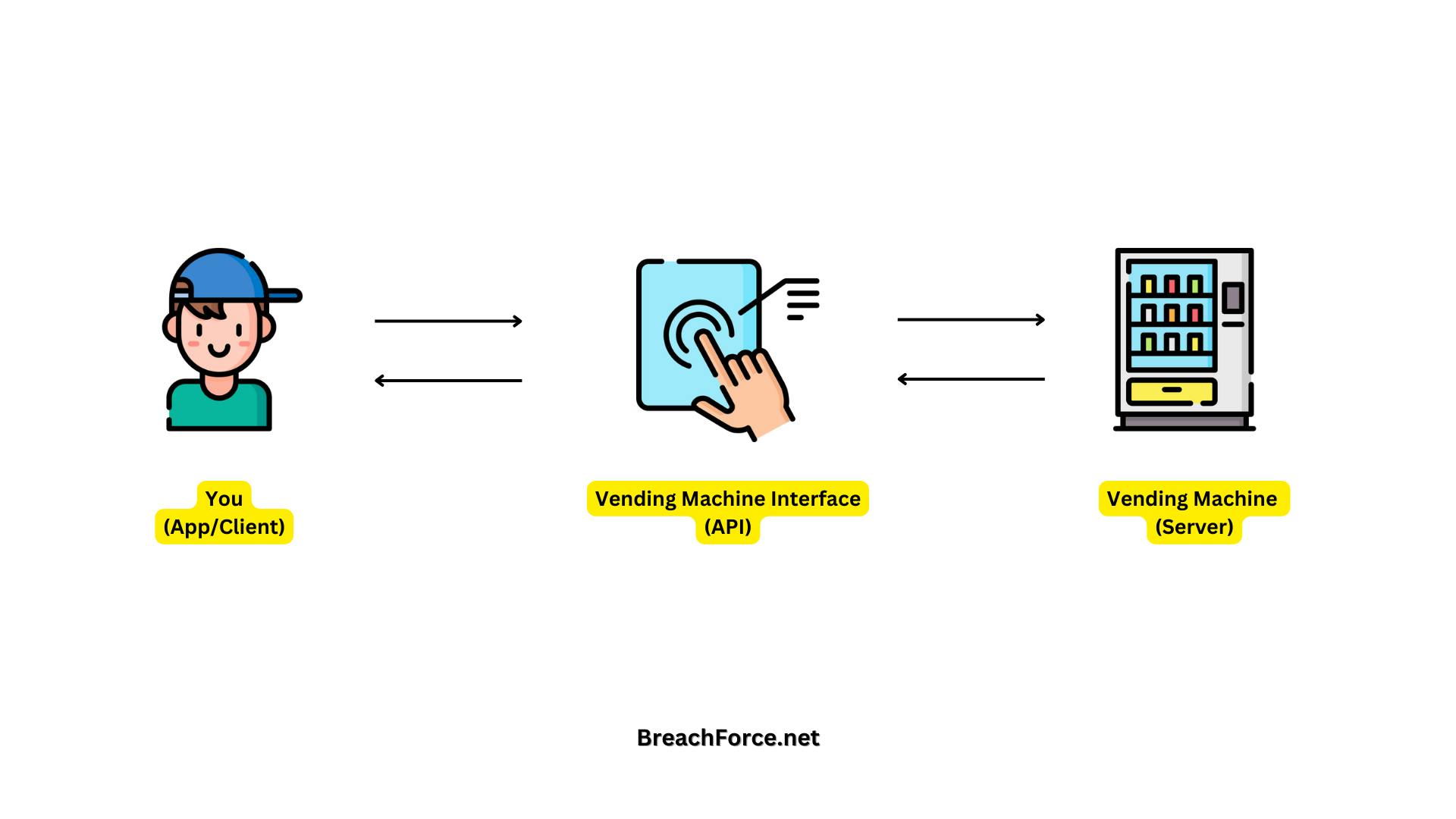
Imagine you are using a smart vending machine (the server) equipped with an interface (API) to interact with it. The vending machine has various slots representing different types of snacks (resources), and you use a digital screen to make selections and provide instructions.
GET Request (Selecting a Snack): You approach the vending machine and use the touch screen to view information about a snack (making a GET request through the API). The machine's API processes your request and displays details about the snack in a simple and standardized format.
POST Request (Adding a Snack): If you want to add a new snack to the machine (creating a resource), you interact with the touch screen, providing the necessary details in a form (making a POST request through the API). The machine's API processes your request and adds the new snack to its inventory.
PUT Request (Updating a Snack): If you decide to change the price or details of an existing snack (updating a resource), you interact with the touch screen, specifying the changes you want (making a PUT request through the API). The machine's API processes your request and adjusts the information accordingly.
DELETE Request (Removing a Snack): If you no longer want a particular snack in the machine (deleting a resource), you interact with the touch screen, selecting the corresponding option (making a DELETE request through the API). The machine's API processes your request and removes that snack from its inventory.
In this refined analogy, the smart vending machine represents the server, the digital screen and touch interface represent the API, each slot is a resource, snacks are the data, and your actions are facilitated through the API using standard HTTP methods.
Key Features of REST API :
REST, an architectural style rather than a protocol, is designed to facilitate communication between systems over the web.
Statelessness: Each request from a client contains all the information needed for the server to understand and fulfill the request.
Resource-Based: Resources (data or services) are identified by URIs (Uniform Resource Identifiers) and are manipulated using standard HTTP methods (GET, POST, PUT, DELETE).
Representation: Resources can be represented in multiple formats, commonly JSON or XML.
Examples of REST API :
GitHub API -
GitHub provides a RESTful API that allows developers to interact with various aspects of the platform programmatically. For instance, you can use the GitHub API to retrieve information about repositories, create issues, or even give a star to a repository
GET https://api.github.com/repos/octocat/hello-world
Twitter API -
Twitter exposes a RESTful API that enables developers to integrate Twitter functionalities into their applications. You can perform actions like tweeting, retrieving user timelines, or searching for tweets.
POST https://api.twitter.com/2/tweets
2. SOAP API: Simple Object Access Protocol
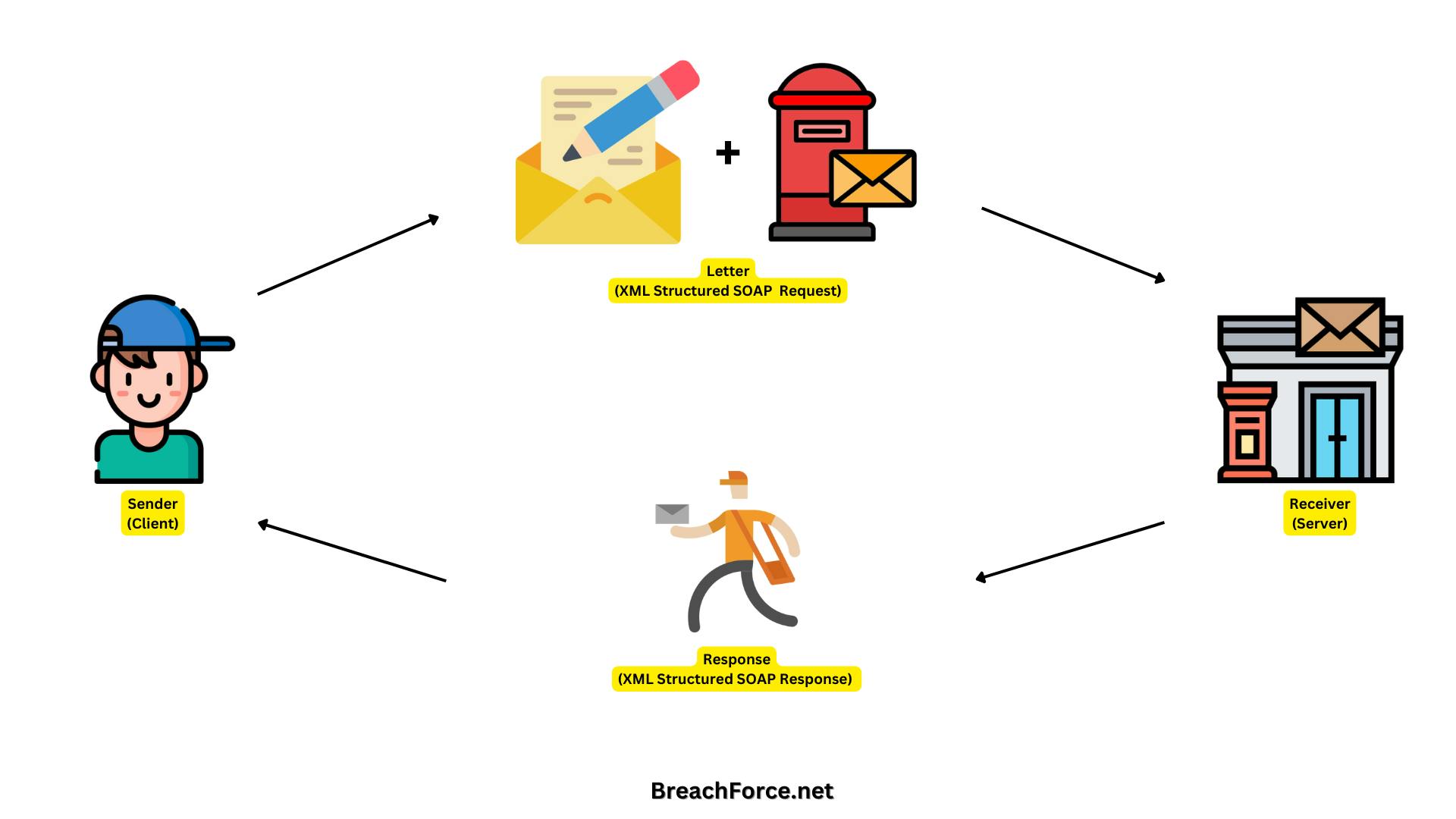
Imagine you are sending a letter through traditional mail (the protocol) to request information from a weather service (the server). You follow a specific format to ensure your message is understood, much like SOAP uses XML for its structured format.
SOAP Request (Sending a Letter) -
You write a letter (SOAP request) to the weather service, stating that you want to know the current weather in a particular city. The letter has a predefined structure (XML format) that the weather service understands.
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://www.example.com/weatherservice">
<soapenv:Header/>
<soapenv:Body>
<web:GetWeather>
<web:City>New York</web:City>
</web:GetWeather>
</soapenv:Body>
</soapenv:Envelope>
SOAP Response (Receiving a Letter Back) -
The weather service processes your request and sends back a response (SOAP response) in the same structured format. It's like receiving a letter in the mail with the requested weather information.
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://www.example.com/weatherservice">
<soapenv:Header/>
<soapenv:Body>
<web:WeatherResponse>
<web:Temperature>25°C</web:Temperature>
<web:Conditions>Sunny</web:Conditions>
</web:WeatherResponse>
</soapenv:Body>
</soapenv:Envelope>
In this analogy, the SOAP envelope is like the letter envelope, the SOAP body is the content of the letter, and the specific SOAP operation (e.g., GetWeather) is equivalent to stating your request. SOAP ensures a structured and standardized way of communication, much like following a specific format when sending and receiving letters through the mail.
Key Features of SOAP API :
SOAP is a protocol for exchanging structured information in web services. Key features of SOAP APIs include
XML-Based Messaging: SOAP messages are formatted in XML, providing a standardized way for applications to communicate.
Complex Operations: SOAP supports complex operations and transactions, making it suitable for enterprise-level applications.
Protocol-Independent: SOAP can be carried over a variety of protocols, including HTTP, SMTP, and more.
OWASP Top 10 API Security Risks :
Navigating and exploring the API OWASP Top 10 for 2023, shedding light on critical security risks. Before diving into the practical configuration of essential tools for API Pentesting, let's examine these identified risks.
API1:2023 - Broken Object Level Authorization
API2:2023 - Broken Authentication
API3:2023 - Broken Object Property Level Authorization
API4:2023 - Unrestricted Resource Consumption
API5:2023 - Broken Function Level Authorization
API6:2023 - Unrestricted Access to Sensitive Business Flows
API7:2023 - Server Side Request Forgery
API8:2023 - Security Misconfiguration
API9:2023 - Improper Inventory Management
API10:2023 - Unsafe Consumption of APIs
For more information kindly visit the OWASP Official Website
Client Pre-requisite :
Before initiating API penetration testing, ensure that clients have the necessary prerequisites.
1. API Documentation -
Thoroughly review the API documentation to gain insights into endpoints, data formats, and authentication mechanisms. A comprehensive understanding of the API's functionality is crucial for effective penetration testing.
2. Postman Collection File (.postman_collection.json) -
Request clients to provide the Postman Collection file (.postman_collection.json) as it serves as a valuable asset during API penetration testing. This file contains details about requests, parameters, and authentication settings.
3. Proper Credentials & Accessibility -
Emphasize the importance of providing proper credentials for authentication during API testing. Accurate credentials enable testers to assess security measures effectively, uncovering any weaknesses related to authentication and authorization.
Additionally, confirming the accessibility of the API whether API is accessible from your system or do you need to whitelist the IP in order to test the API.
Setting Up Burp Suite for API Pentesting :
1. Download and Install Burp Suite.
Visit the PortSwigger website to download the community version of Burp Suite.
If you want to use the professional version you can buy the license or get the cracked version from Telegram. (https://t.me/burpsuite)
2. Download and Install Postman.
Visit the Postman website to download the latest version of Postman.
3. In Postman, go to "Settings" and then "Proxy."
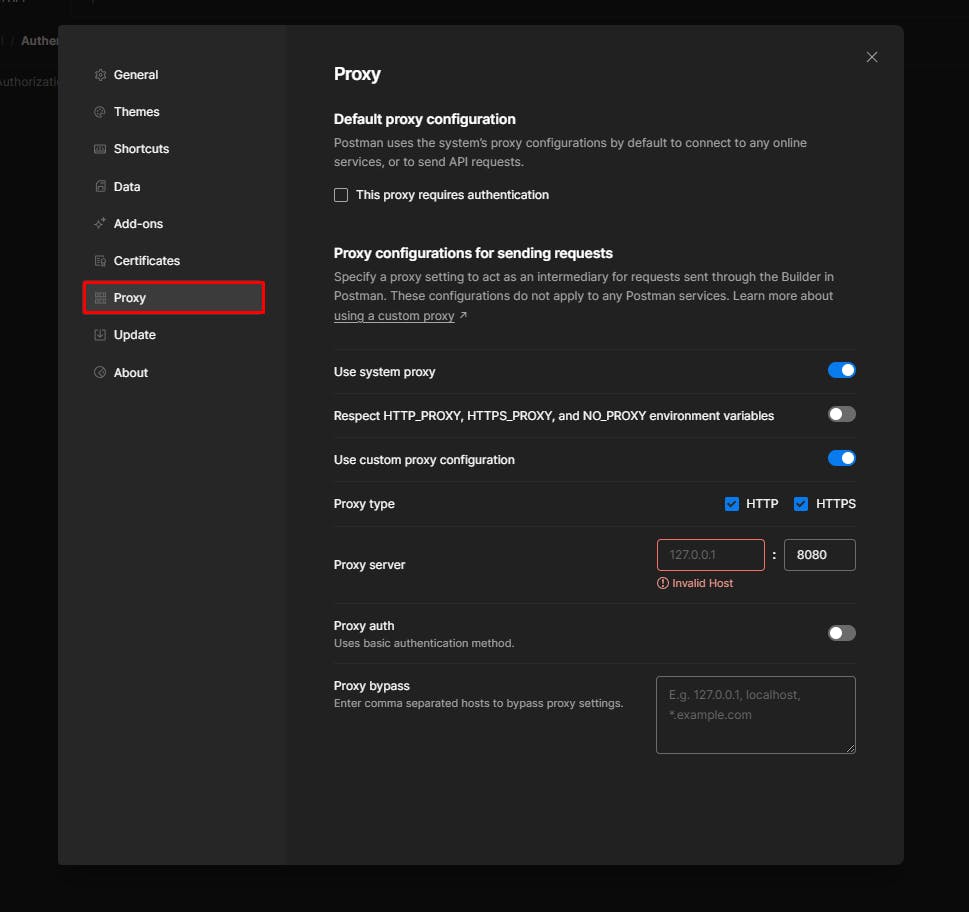
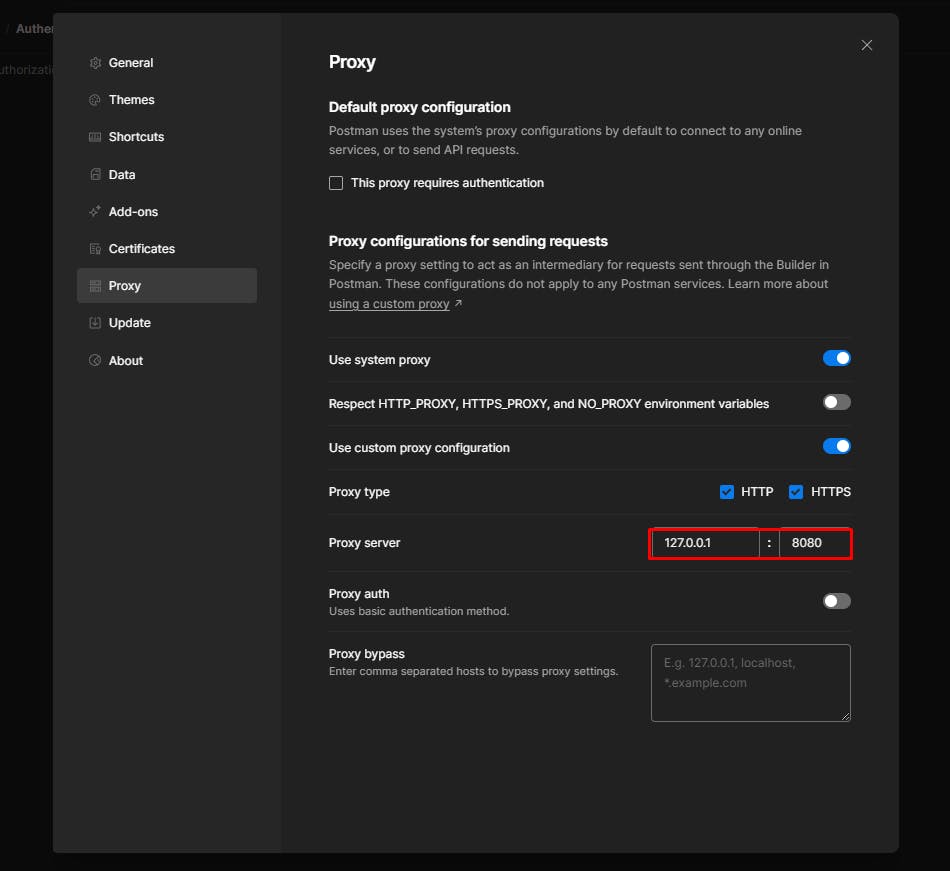
4. Set the proxy to 127.0.0.1 the port you noted in Burp Suite (usually 8080).
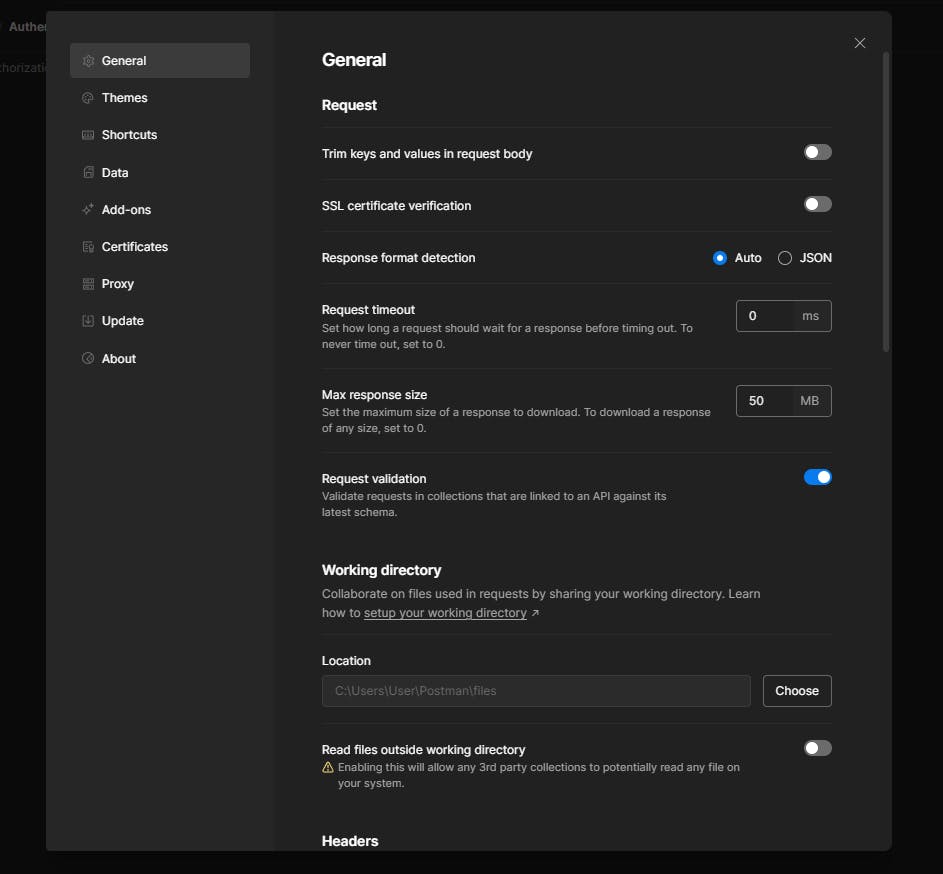
5. Sometimes by default SSL verification is enabled in Postman. Go to general and turn it off.
6. Verify IP and port in BurpSuite.
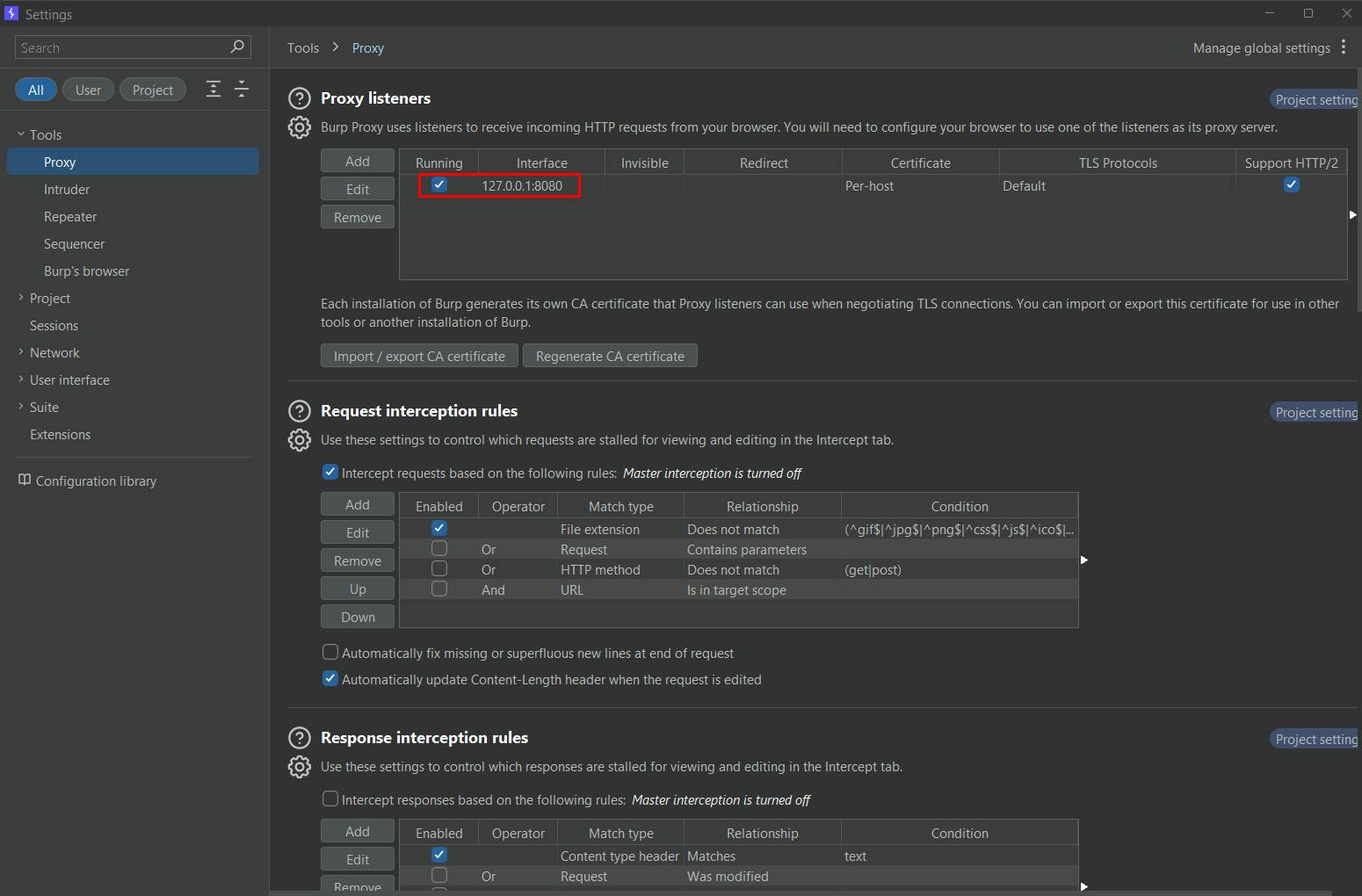
7. Now, when you send requests from Postman, Burp Suite will intercept them, allowing you to analyze and manipulate the requests and responses.
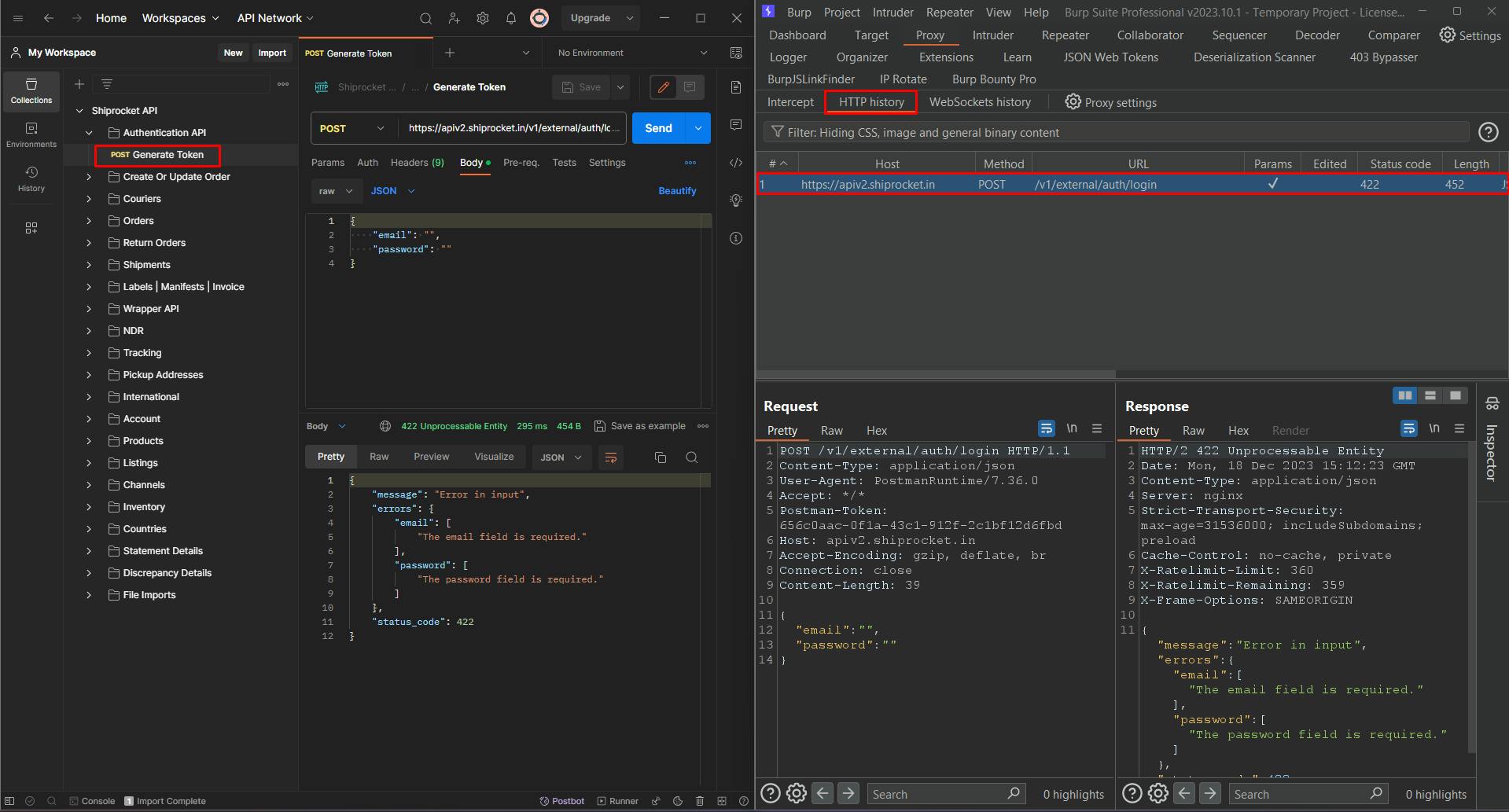
Note - The public API collection shown in the screenshot is utilized for demonstration purposes.
Automating API Pentesting :
As we navigate the landscape of API security, it's important to not only identify vulnerabilities but also to streamline the testing process. Automation emerges as a key player in this pursuit, offering efficiency and consistency in uncovering potential threats.
APIs are dynamic entities, and manual testing can be time-consuming. Automation enhances the testing lifecycle by providing speed, repeatability, and scalability.
For a comprehensive guide on setting up your API pen-testing automation environment using Pynt, check out this insightful video tutorial.
Conclusion :
In conclusion, mastering API security involves understanding the intricacies of REST and SOAP APIs, addressing the OWASP Top 10 risks, and leveraging powerful testing tools.
References :
API Security Checklist - https://github.com/Cyber-Guy1/API-SecurityEmpire/tree/main/assets
API Security Best Practices - https://github.com/shieldfy/API-Security-Checklist
Vulnerable API For Testing - https://github.com/roottusk/vapi
