Scenarios
Introduction
During red team activities, there may be instances where you encounter limitations on downloading and uploading from your laptop due to the presence of web proxies and Data Loss Prevention (DLP) measures.
At times, DLP systems may identify the transmission of PII data in clear text; hence, encoding the data in Base64 before posting can help avoid detection.
Reference: T1567.003 - Exfiltration Over Web Service: Exfiltration to Text Storage Sites
More Details on T1567.003
pastebin[.]com, is commonly used by developers to share code and other information.Text storage sites are often used to host malicious code for C2 communication (e.g., Stage Capabilities), but adversaries may also use these sites to exfiltrate collected data. Furthermore, paid features and encryption options may allow adversaries to conceal and store data more securely. (Citation: Pastebin EchoSec)
Ways to circumvent such restrictions
Pre-requisites for this activity
PowerShell
The objective is to bypass restrictions to identify websites on restricted devices where text can be stored, such as Medium, GitLab, GitHub, or any platform allowing comments or text posting.
Refer This: https://lots-project.com/
~mrd0x
Upon identifying such a website, we can proceed to extract or introduce data in text format, either by exfiltrating or infiltrating files or documents from the restricted device.
Time to exfiltrate data
To encode data in PowerShell and encode it in Base64 format, use the following commands:
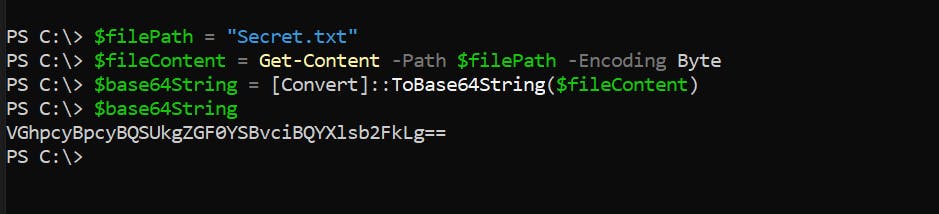
# Specify the path to the file you want to convert
$filePath = "C:\Path\To\Your\File.txt"
# Read the file content
$fileContent = Get-Content -Path $filePath -Encoding Byte
# Convert to Base64
$base64String = [Convert]::ToBase64String($fileContent)
# Output the Base64 string
$base64String
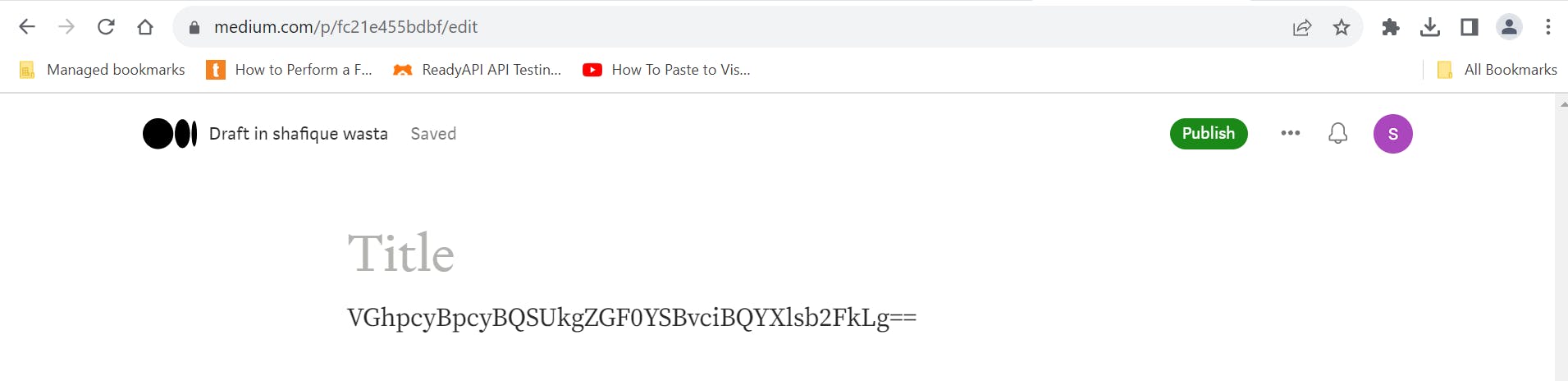
Post or comment on this base64 data as text where you found the text storage
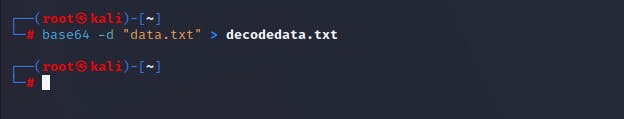
Get the text data in your system and Decrypt the data.



Conclusion:
Data exfiltration without file uploads renders DLP incapable of detecting the activity since no files are being uploaded.
