Red Teaming: The Art of Active Directory Enumeration
Step-by-step Active directory enumeration guide after getting an initial foothold
Table of contents
- Introduction :
- Identify Domain Controller :
- Enumerating Active Directory with In-built PowerShell Commands :
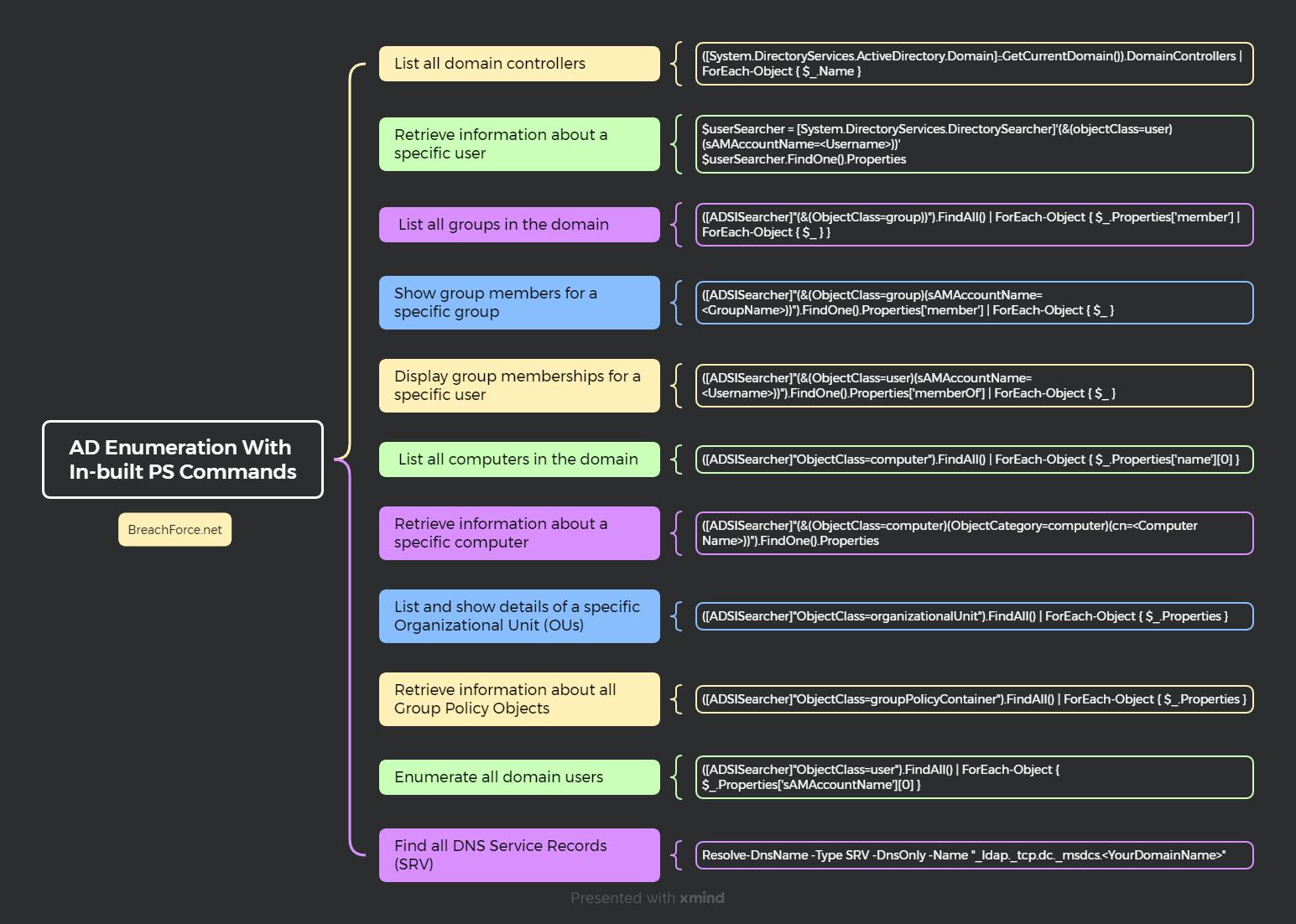
- 1. List all domain controllers
- 2. Retrieve information about a specific user
- 3. List all groups in the domain:
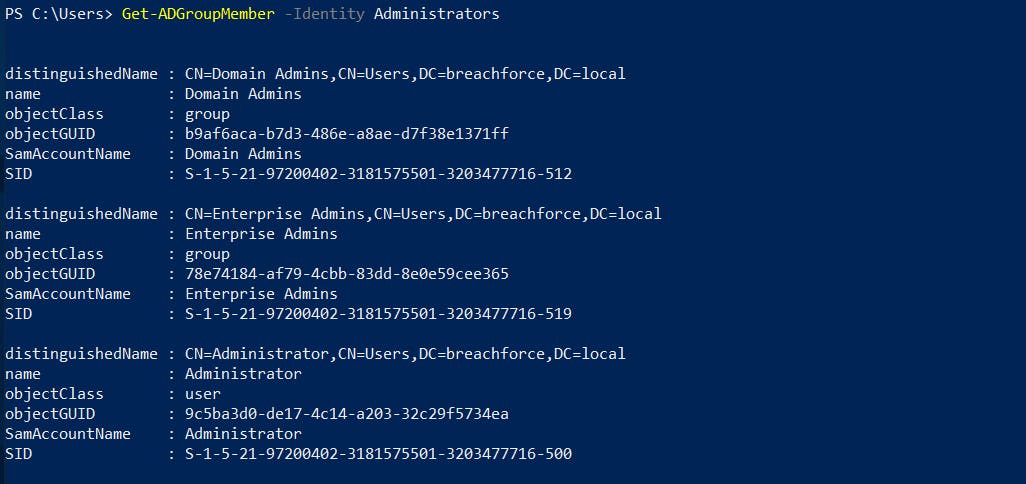
- 4. Show group members for a specific group
- 5. Display group memberships for a specific user
- 6. List all computers in the domain
- 7. Retrieve information about a specific computer
- 8. List and show details of a specific Organizational Unit (OUs)
- 9. Retrieve information about all Group Policy Objects
- 10. Enumerate all domain users
- 11. Find all DNS Service Records (SRV)
- Enumerating Active Directory Using AD Module :
- 1. List all domain controllers
- 2. Retrieve information about a specific user
- 3. List all groups in the domain
- 4. Show group members for a specific group
- 5. Display group memberships for a specific user
- 6. List all computers in the domain
- 7. Retrieve information about a specific computer
- 8. List and show details of a specific Organizational Unit (OUs)
- 9. Retrieve information about all Group Policy Objects
- 10. Enumerate all domain users
- Enumerating Active Directory Using Command Prompt :
- Enumerating Active Directory Using External PowerShell Scripts :
- Conclusion :
Introduction :
In the ever-evolving landscape of cybersecurity, red teaming has emerged as a pivotal practice for organizations seeking to fortify their defenses against potential threats. Among the arsenal of techniques employed during red team assessments, the art of enumeration stands out as a crucial phase in the reconnaissance process.
Upon gaining entry to the network and obtaining access to a machine within the domain using a low-privileged user with PowerShell capabilities, we can start our enumeration process can be initiated.
Enumeration, the process of extracting valuable information about a target network, lays the foundation for subsequent stages of a red teaming engagement. It involves meticulous reconnaissance, where every bit of data becomes a potential key to unlocking vulnerabilities.
Identify Domain Controller :
Before we dive into the main content of the blog, let's explore various techniques that can be employed to identify Domain Controllers (DC) within large networks.
1. Obtaining the Domain Name
1.1 Right-click on "This PC" or "Computer," go to Properties, and inspect the Full Computer Name.
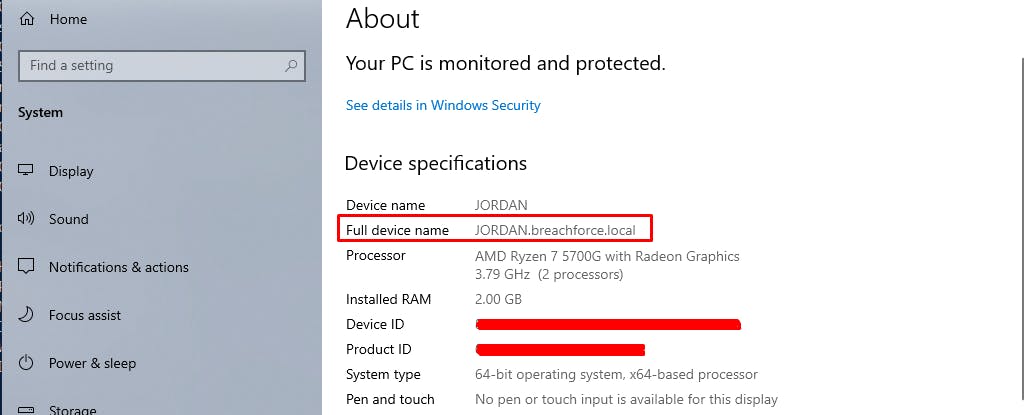
1.2 Command Prompt
echo %userdomain%

1.3 IP Configuration
ipconfig /all
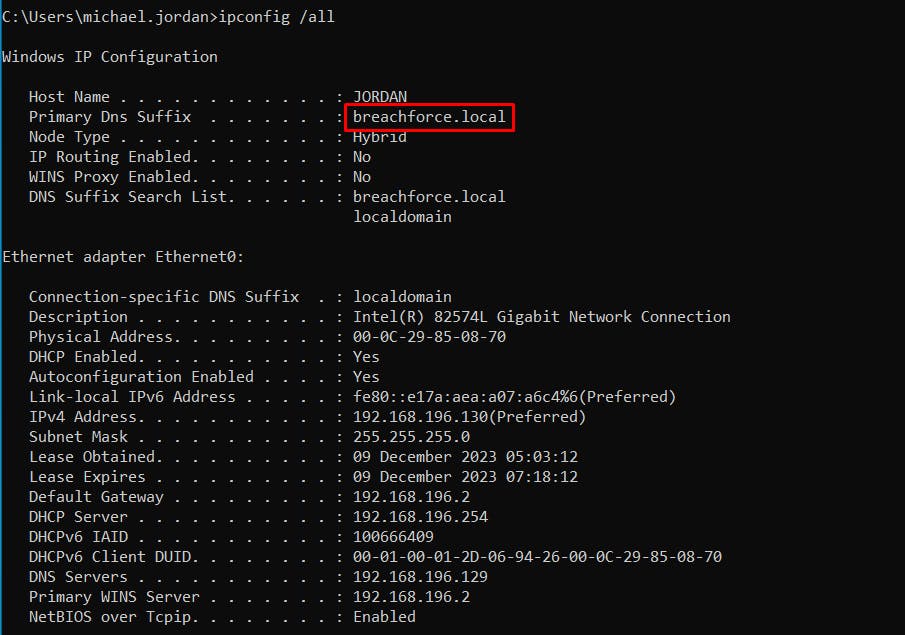
2. Identifying Domain Controllers
2.1 DNS Records
nslookup -type=SRV _ldap._tcp.<YourDomainName>
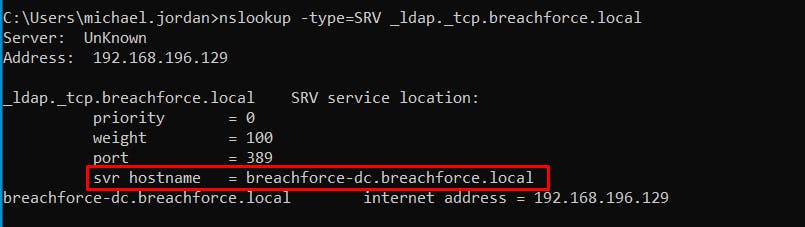
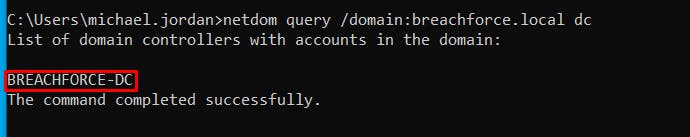
2.2 NetDom Command
netdom query /domain:<YourDomainName> dc
Enumerating Active Directory with In-built PowerShell Commands :
When it comes to enumeration, red teamers often face constraints, especially in environments where running external PowerShell scripts may be restricted due to security policies. However, there are built-in PowerShell commands that can adeptly navigate the intricate landscape of AD without relying on external scripts.
1. List all domain controllers
([System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()).DomainControllers | ForEach-Object { $_.Name }
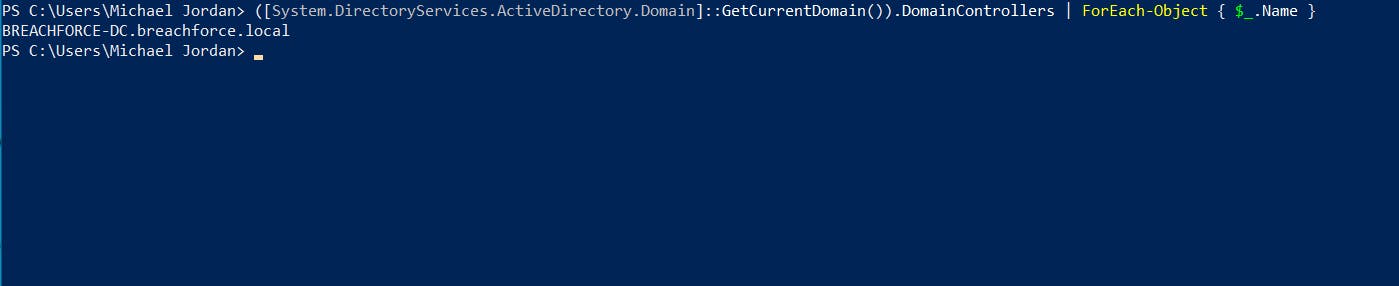
2. Retrieve information about a specific user
$userSearcher = [System.DirectoryServices.DirectorySearcher]'(&(objectClass=user)(sAMAccountName=<Username>))'
$userSearcher.FindOne().Properties
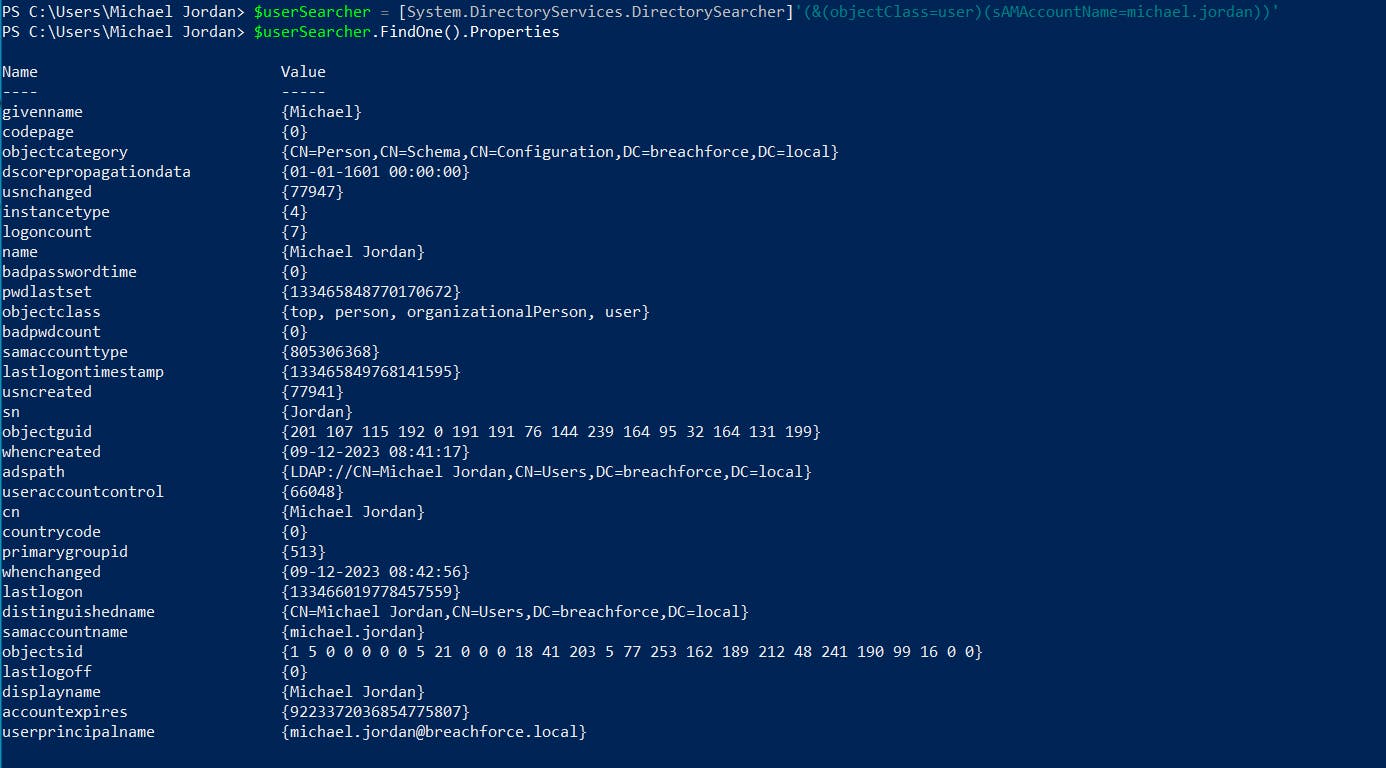
3. List all groups in the domain:
([ADSISearcher]"(&(ObjectClass=group))").FindAll() | ForEach-Object { $_.Properties['member'] | ForEach-Object { $_ } }
4. Show group members for a specific group
([ADSISearcher]"(&(ObjectClass=group)(sAMAccountName=<GroupName>))").FindOne().Properties['member'] | ForEach-Object { $_ }
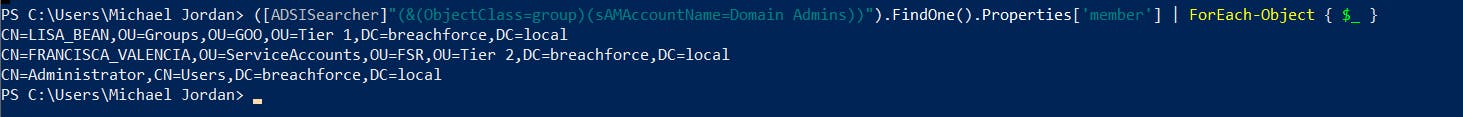
5. Display group memberships for a specific user
([ADSISearcher]"(&(ObjectClass=user)(sAMAccountName=<Username>))").FindOne().Properties['memberOf'] | ForEach-Object { $_ }

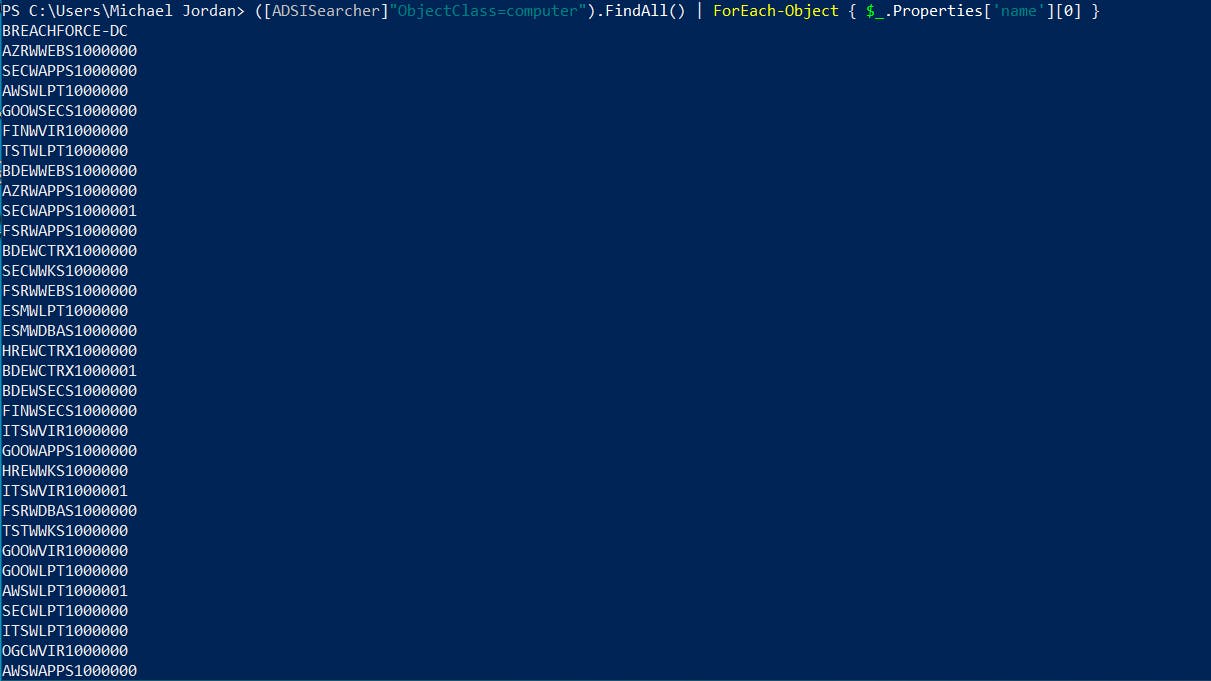
6. List all computers in the domain
([ADSISearcher]"ObjectClass=computer").FindAll() | ForEach-Object { $_.Properties['name'][0] }
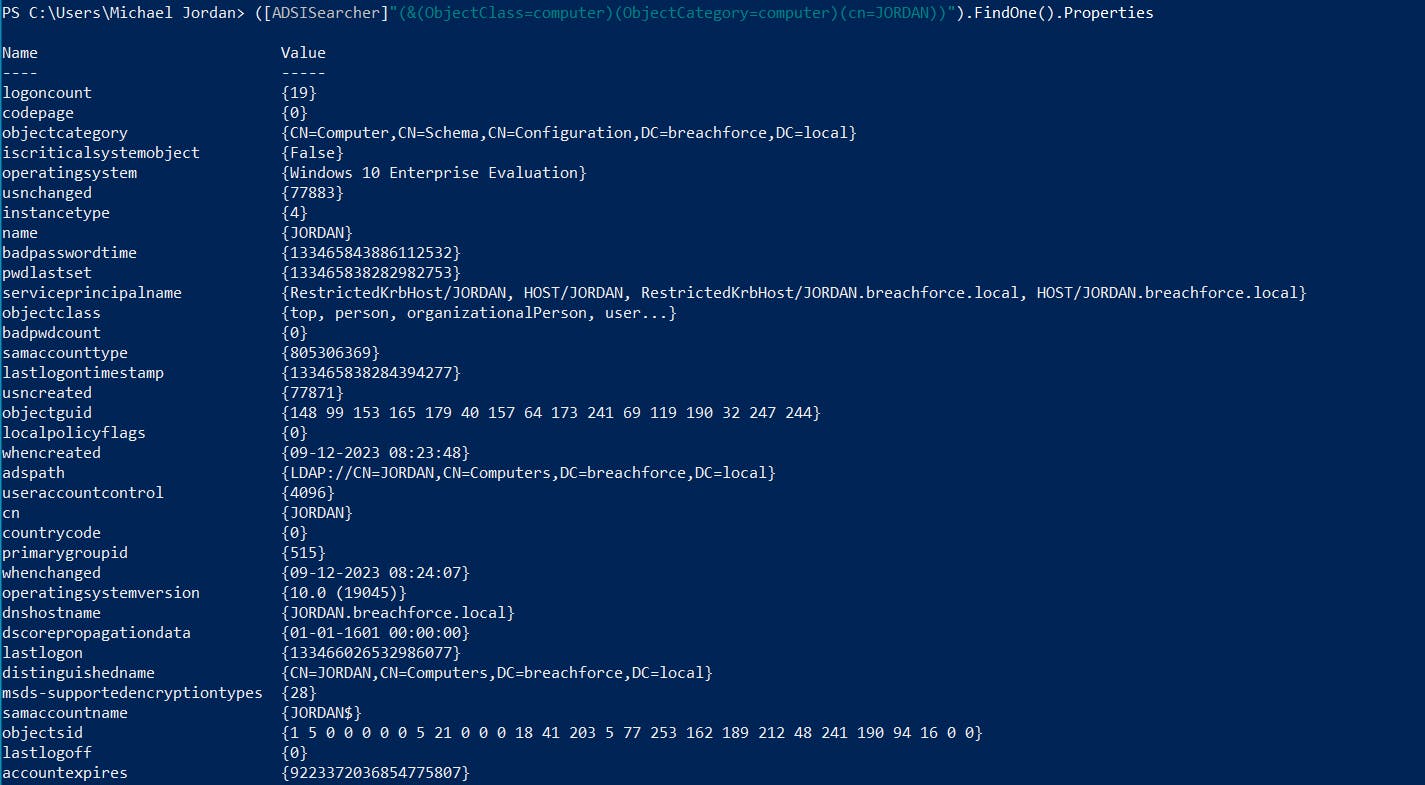
7. Retrieve information about a specific computer
([ADSISearcher]"(&(ObjectClass=computer)(ObjectCategory=computer)(cn=<Computer Name>))").FindOne().Properties
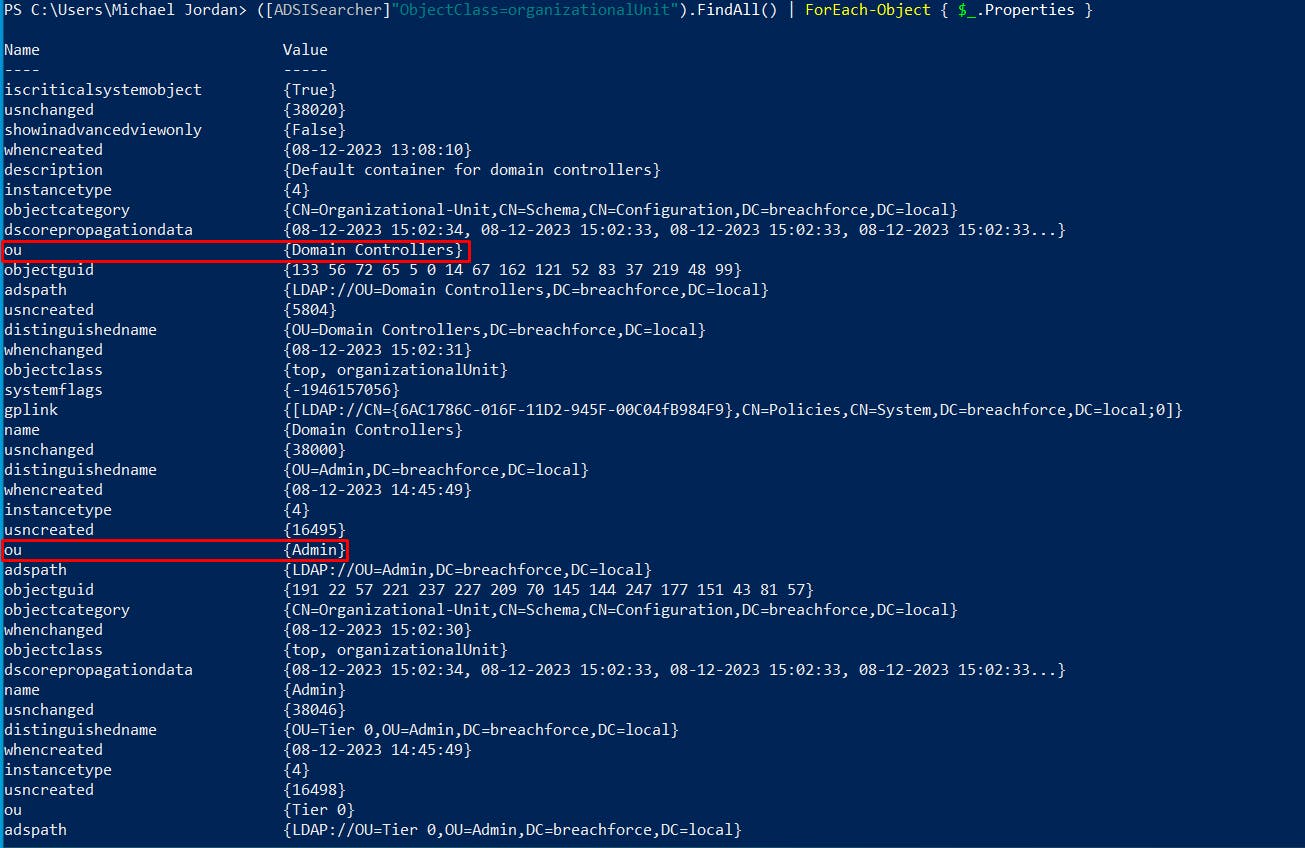
8. List and show details of a specific Organizational Unit (OUs)
([ADSISearcher]"ObjectClass=organizationalUnit").FindAll() | ForEach-Object { $_.Properties }
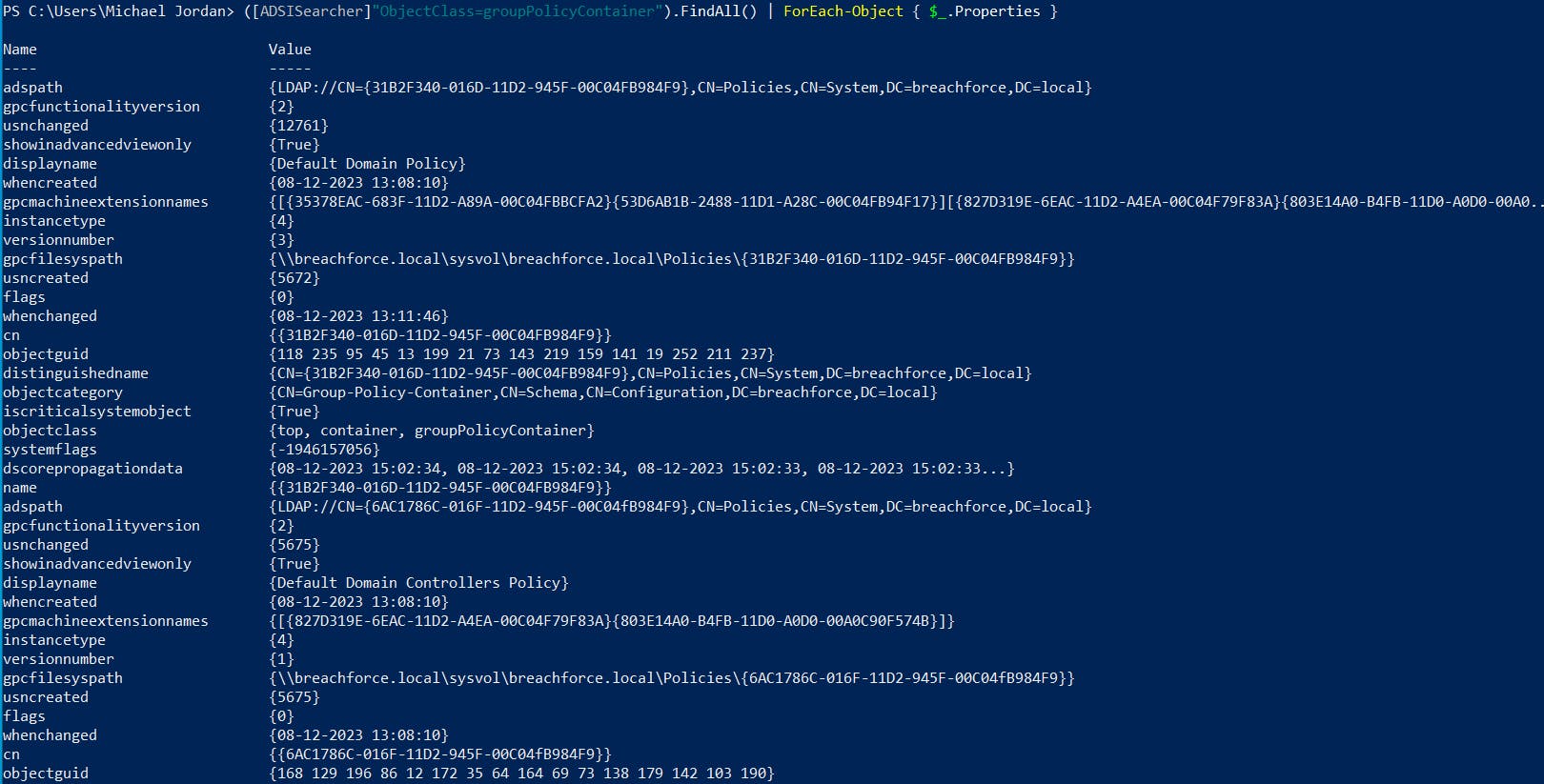
9. Retrieve information about all Group Policy Objects
([ADSISearcher]"ObjectClass=groupPolicyContainer").FindAll() | ForEach-Object { $_.Properties }
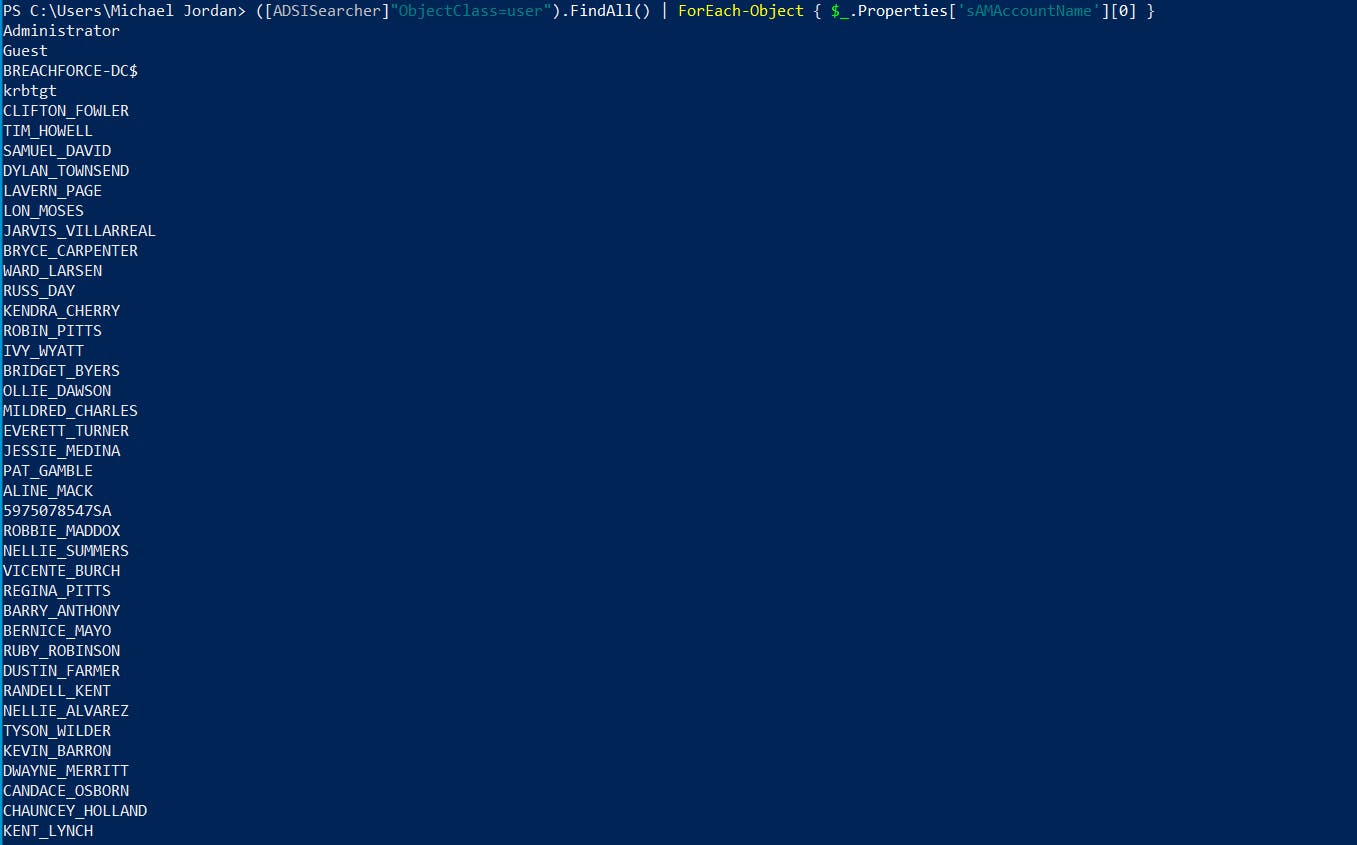
10. Enumerate all domain users
([ADSISearcher]"ObjectClass=user").FindAll() | ForEach-Object { $_.Properties['sAMAccountName'][0] }
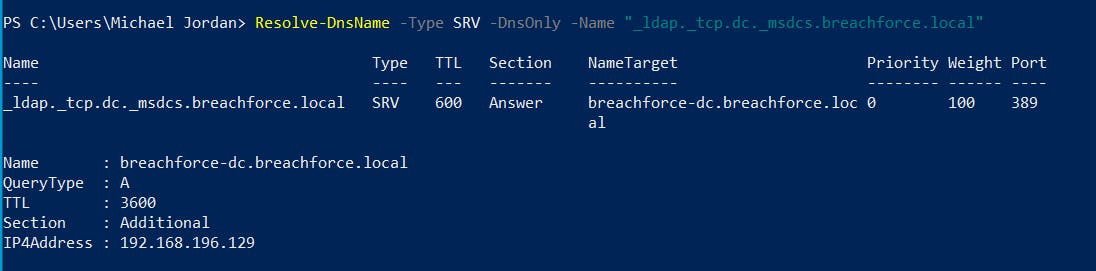
11. Find all DNS Service Records (SRV)
Resolve-DnsName -Type SRV -DnsOnly -Name "_ldap._tcp.dc._msdcs.<YourDomainName>"
Enumerating Active Directory Using AD Module :
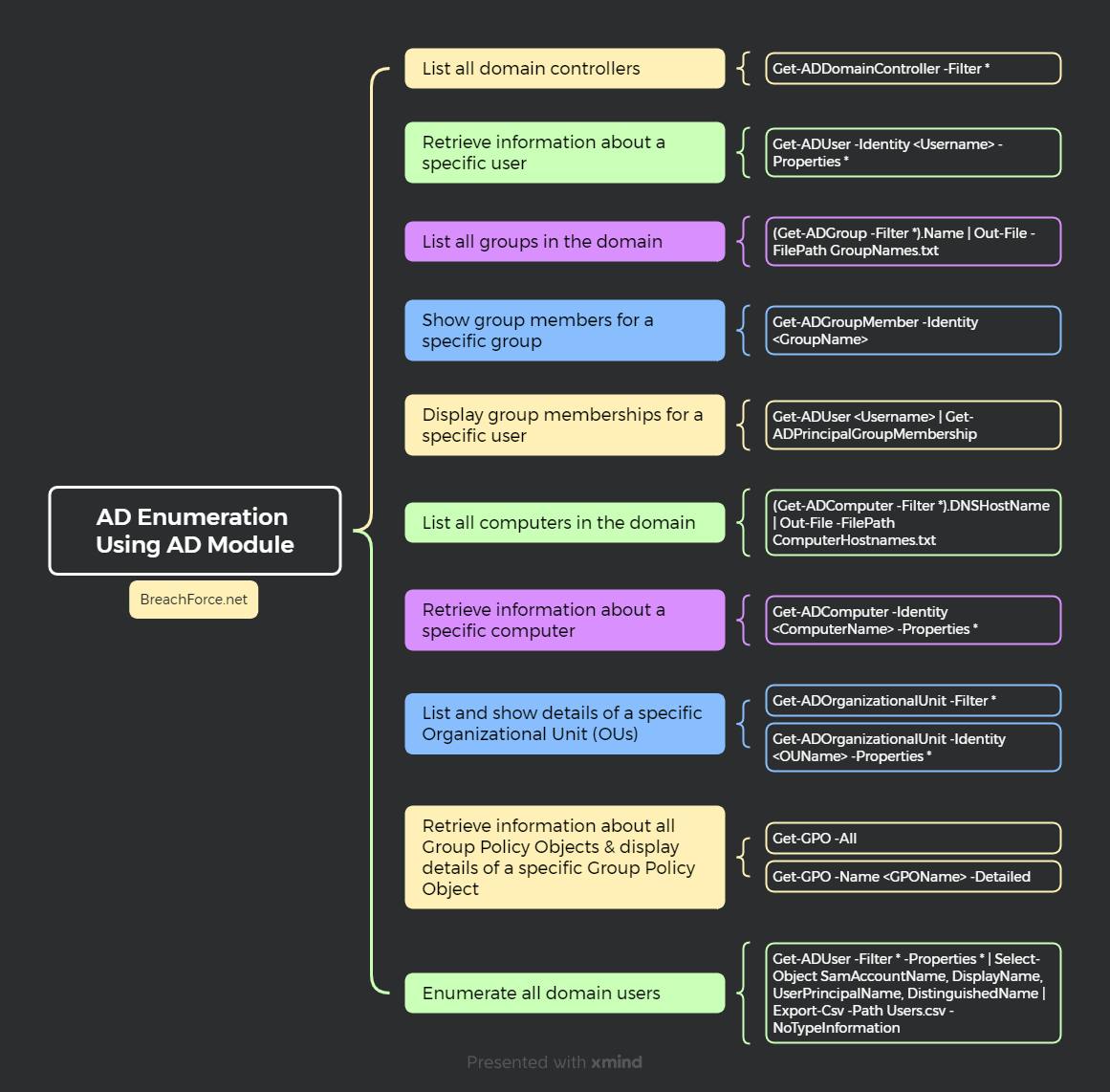
Leveraging the Active Directory module is a key tactic in efficient enumeration. This tool equips practitioners with precise commands to navigate and extract valuable insights from Active Directory, a critical aspect of comprehensive security assessments.
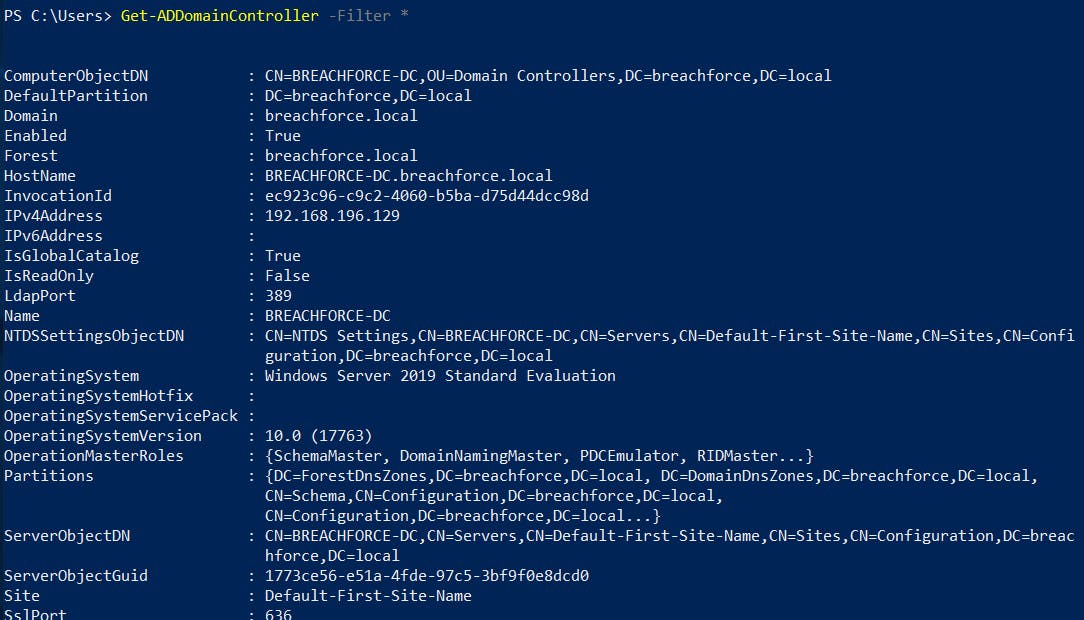
1. List all domain controllers
Get-ADDomainController -Filter *
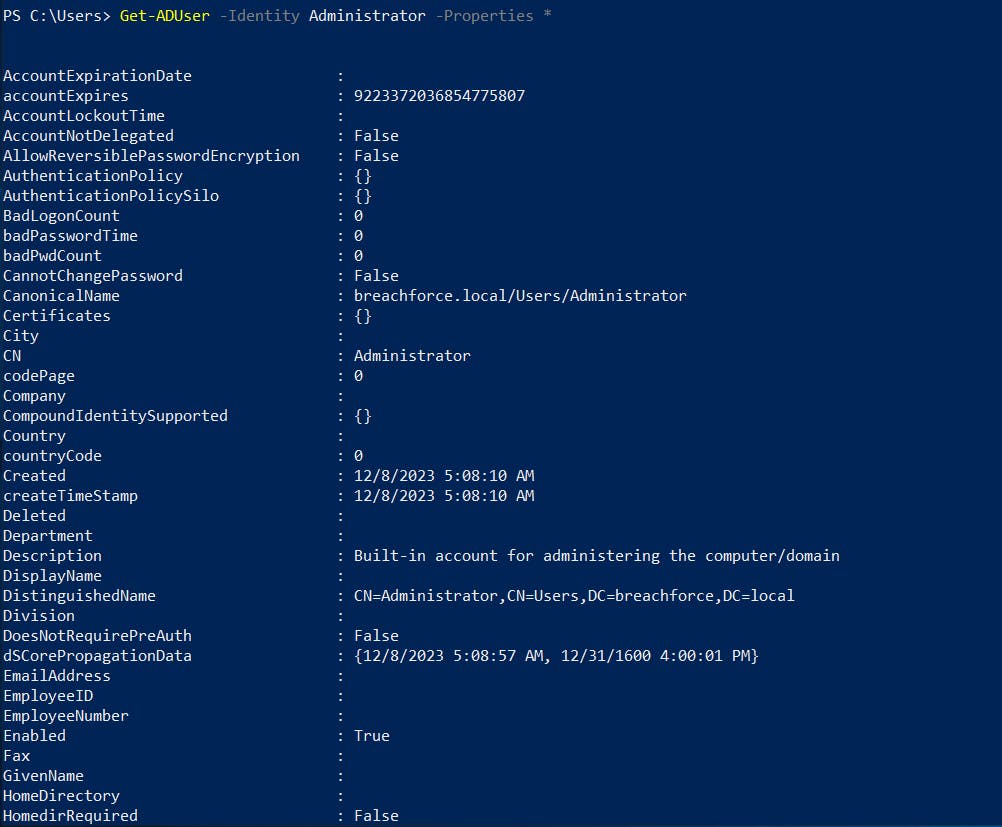
2. Retrieve information about a specific user
Get-ADUser -Identity <Username> -Properties *
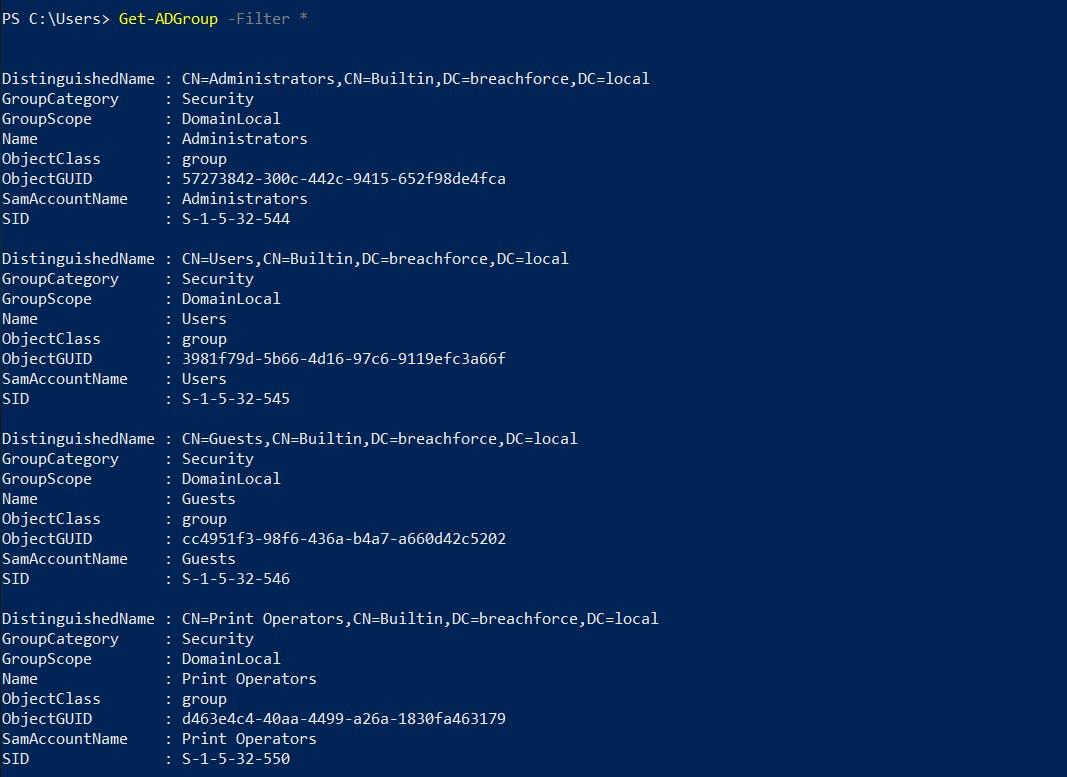
3. List all groups in the domain
Get-ADGroup -Filter *
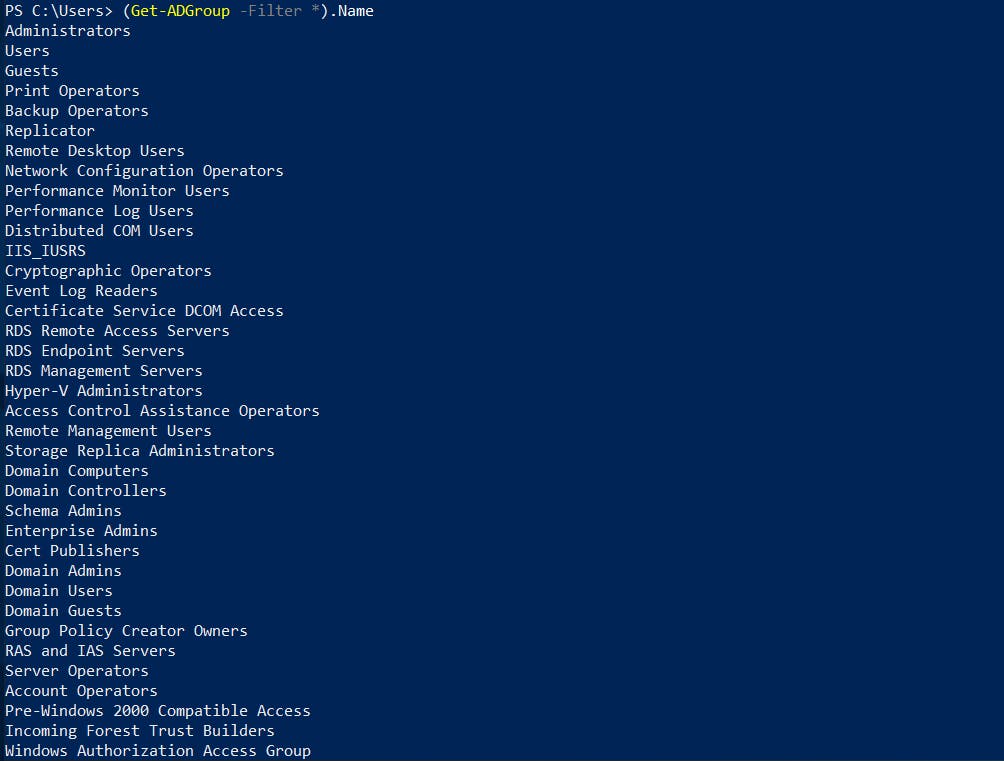
# Enumerate all the Group names and save it in a file
(Get-ADGroup -Filter *).Name | Out-File -FilePath GroupNames.txt
4. Show group members for a specific group
Get-ADGroupMember -Identity <GroupName>
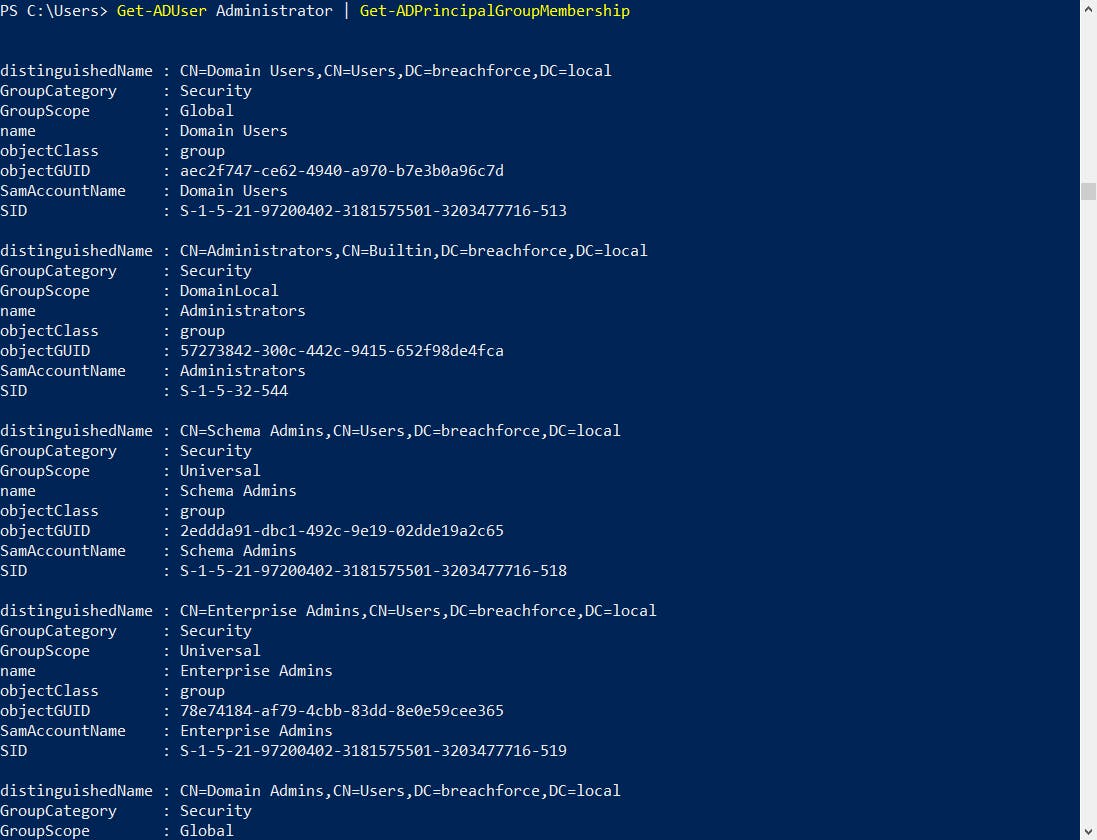
5. Display group memberships for a specific user
Get-ADUser <Username> | Get-ADPrincipalGroupMembership
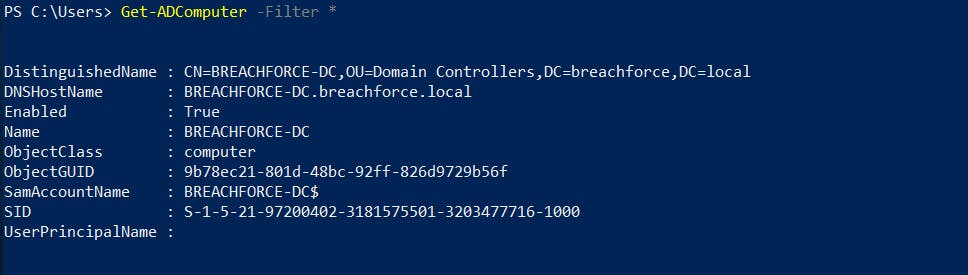
6. List all computers in the domain
Get-ADComputer -Filter *
# Enumerate all the Computer host names and save it in a file
(Get-ADComputer -Filter *).DNSHostName | Out-File -FilePath ComputerHostnames.txt
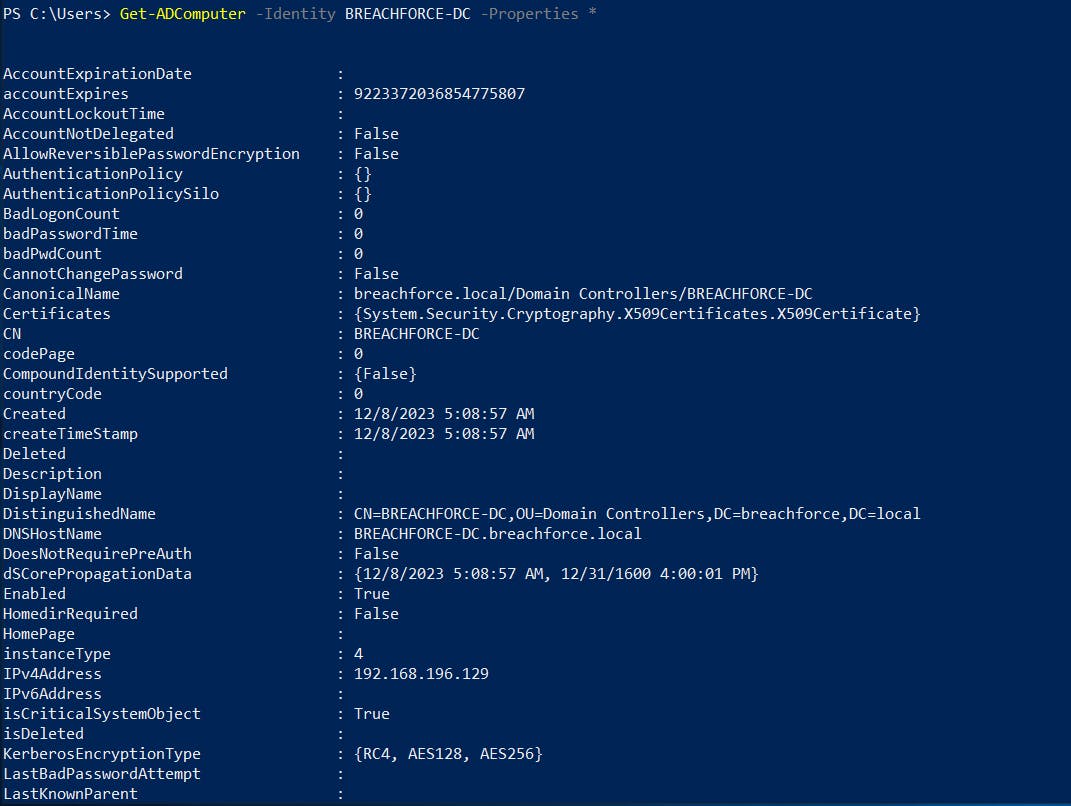
7. Retrieve information about a specific computer
Get-ADComputer -Identity <ComputerName> -Properties *
8. List and show details of a specific Organizational Unit (OUs)
Get-ADOrganizationalUnit -Filter * Get-ADOrganizationalUnit -Identity <OUName> -Properties *
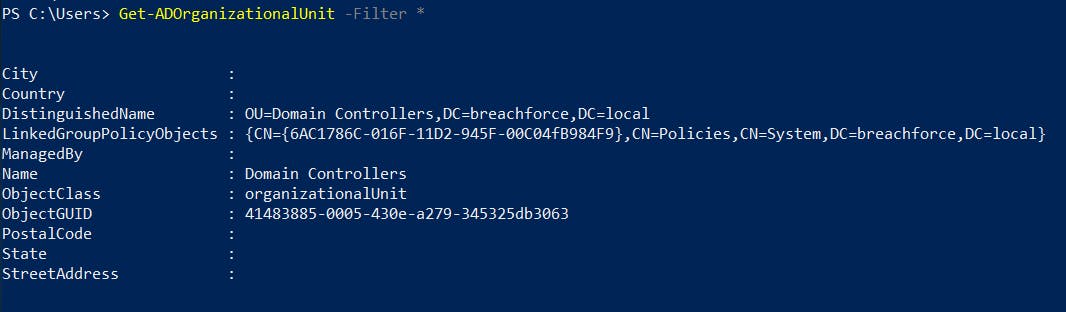
9. Retrieve information about all Group Policy Objects
# Group Policy Objects & display details of a specific Group Policy Object
Get-GPO -All Get-GPO -Name <GPOName> -Detailed
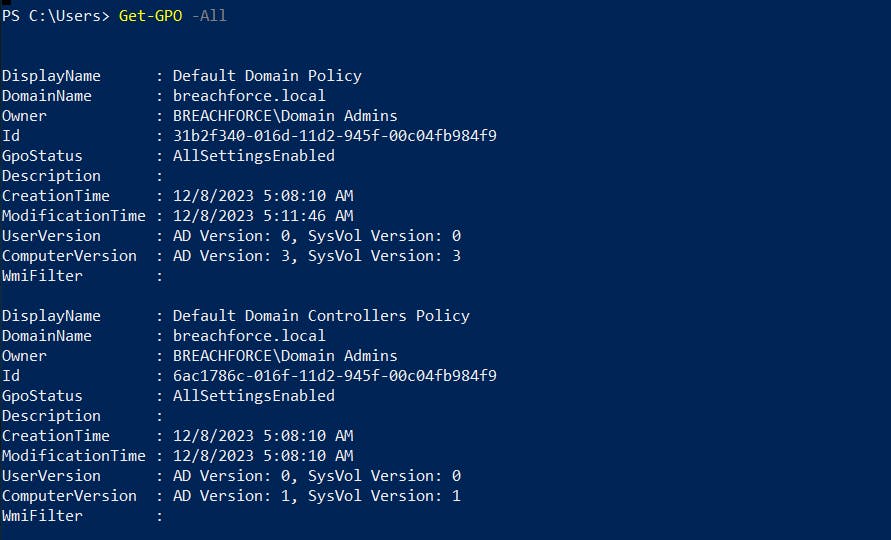
10. Enumerate all domain users
Get-ADUser -Filter * -Properties * | Select-Object SamAccountName, DisplayName, UserPrincipalName, DistinguishedName | Export-Csv -Path C:\Path\To\Save\Users.csv -NoTypeInformation
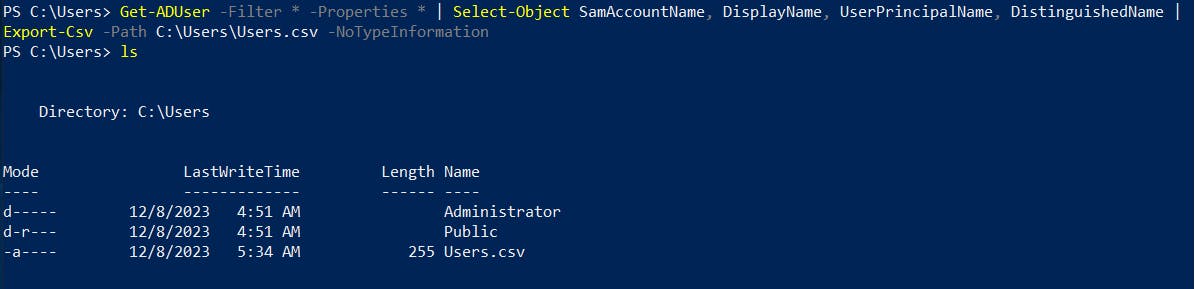
Note: If you want to save the output of each file you can add this cmdlet at the end of each command - | Out-File -FilePath "NameOfFile.txt"
Enumerating Active Directory Using Command Prompt :
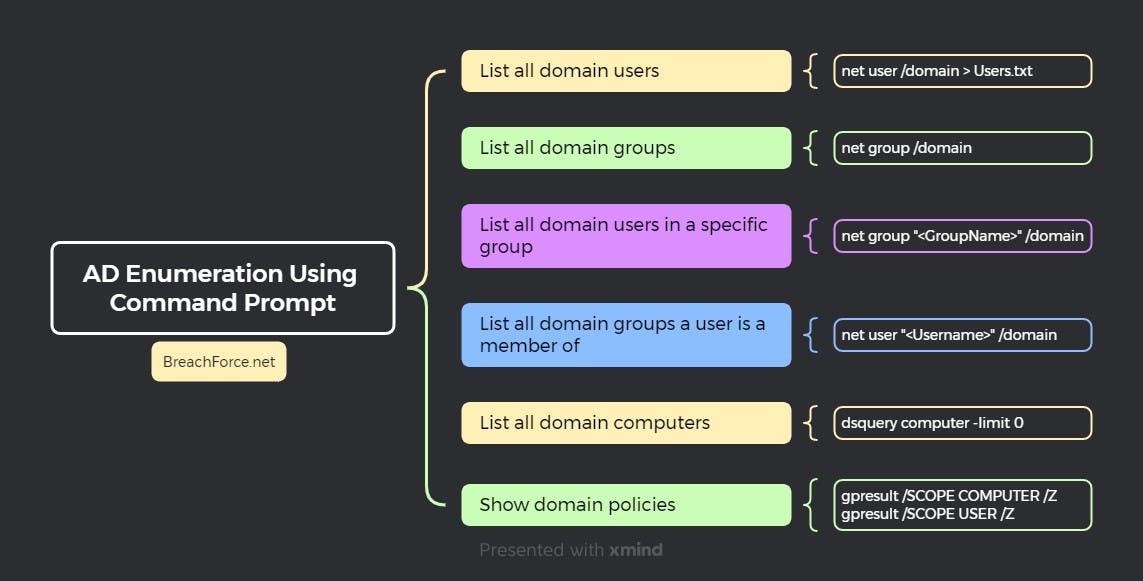
1. List all domain users
net user /domain > Users.txt
2. List all domain groups
net group /domain
3. List all domain users in a specific group
net group "<GroupName>" /domain

4. List all domain groups a user is a member of
net user "<Username>" /domain
5. List all domain computers
dsquery computer -limit 0
6. Show domain policies
gpresult /SCOPE COMPUTER /Z
gpresult /SCOPE USER /Z
Note: If you want to save any output in cmd just give > filename.txt at the end of the command
Enumerating Active Directory Using External PowerShell Scripts :
While native PowerShell commands offer a robust foundation, the realm of possibilities expands exponentially with the incorporation of external PowerShell scripts.
In the real world of cybersecurity, exploring Active Directory can be tricky. We often run into issues like EDR (Endpoint Detection and Response) flags and antivirus roadblocks. Figuring out how to get around these defenses takes time that we usually don't have in urgent situations.
In our journey, we need to recognize that testing external PowerShell scripts, like PowerView and PowerViewDev, is essential. These scripts help us look into Active Directory beyond the basics. However, there are challenges; EDR might spot these scripts, and antivirus tools could raise alarms. So, our path involves using these scripts for exploration while dealing with the security measures in place.
AMSI bypass (amsi.fail)
Obfuscating/Breaking PowerShell scripts
Conclusion :
In conclusion, the blog highlights the crucial role of enumeration in red teaming for fortifying cybersecurity defenses. While in-built PowerShell commands offer a solid foundation for Active Directory exploration, the real-world landscape introduces challenges, necessitating the use of external scripts like PowerView.